On top of dealing with a global pandemic and the challenges that working from home poses for IT administrators, the past few months have seen quite a few alarming vulnerabilities. One of the most critical was announced in August of this year and dubbed the Zerologon vulnerability. What is it and how can organizations ensure the remote workforce is patched and safe from Zerologon?
What is Zerologon Vulnerability?
Let’s consider the Zerologon vulnerability and see why this particular security risk is so alarming. The name Zerologon has been given to a security vulnerability that is detailed in CVE-2020-1472. The name Zerologon comes from the way the vulnerability works and the method used to exploit it. It was discovered by a Dutch security researcher named Tom Tervoort, working for . The official CVE-2020-1472 states the :
“An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.
To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access. Microsoft is addressing the vulnerability in a phased two-part rollout. These updates address the vulnerability by modifying how Netlogon handles the usage of Netlogon secure channels.”
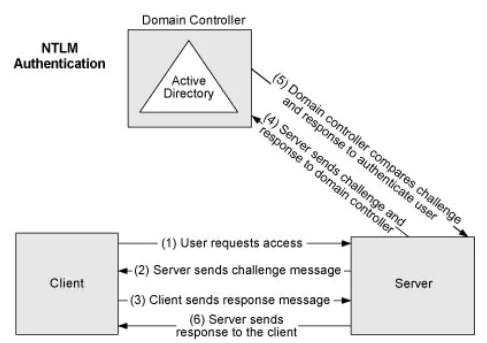
It describes a flaw in the logon process involving Microsoft’s Active Directory Netlogon Remote Protocol (MS-NRPC). This is the protocol that allows users to log on to servers using the NTLM (NT LAN Manager). While NTLM in itself is involved in several important mechanisms in Active Directory, it is also used to transmit account changes that also include computer service account passwords.
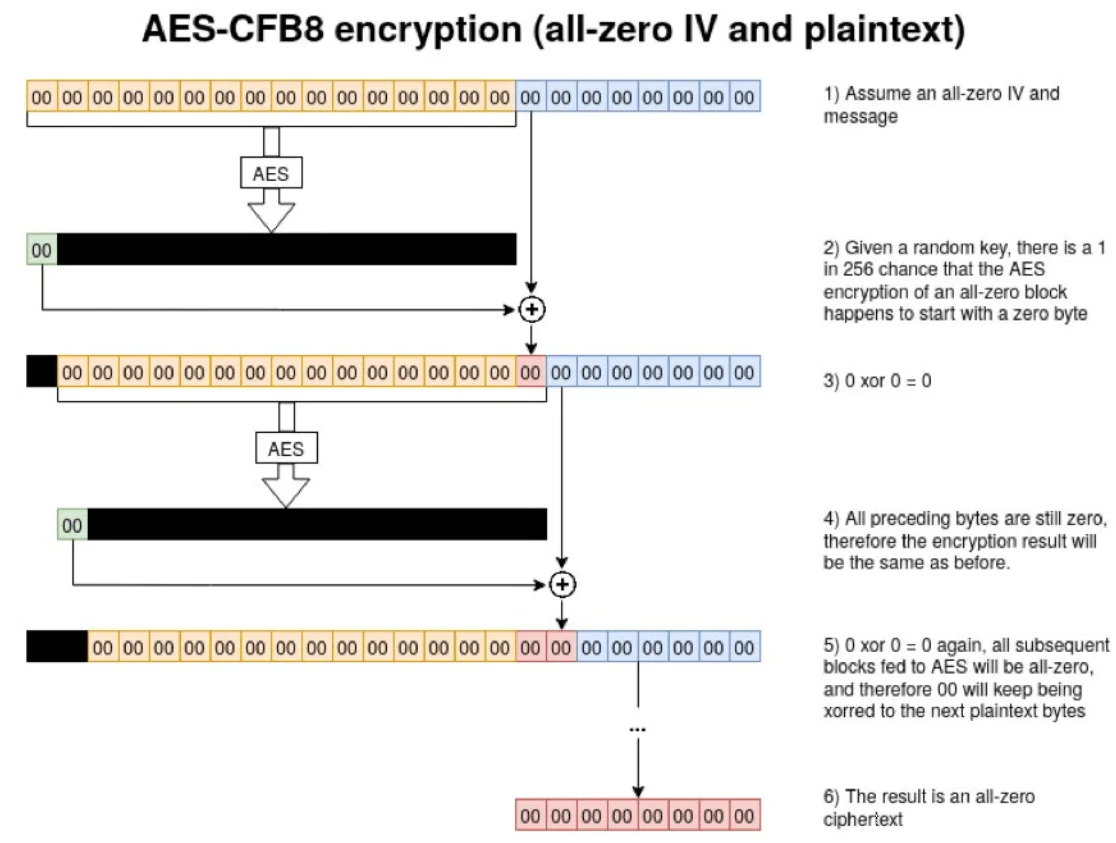
Today, while MS-NRPC uses AES encryption which is standard encryption considered to be strong, it uses a setting called AES-CFB8. This is an obscure standard that is not well tested and in fact, has an issue with the initialization vector (IV) using a fixed value of 16 bytes of zeros in a predictable number of attempts. This predictable pattern makes the cryptography easily broken.
How does the attack work and how would an attacker be able to compromise your network by using a proof of concept? The attacker would need to be inside the network at least in a way to set up a TCP session to one of your domain controllers. Most would achieve this if they have compromised a workstation on the internal LAN and were able to remotely access the workstation. Additionally, physical access to the network would also work, albeit would probably less likely than a remote attack.
Tom Tervoort found that when using AES-CFB8 with a fixed initialization vector (IV) of 16 bytes with all zeros, one in every 256 keys used will create a ciphertext that has a value of all zeros. In the world of hacking and exploitation, this is an incredibly small number of attempts to create a successful attempt that would generate all zeros cipher text.
The attacker then carries out a few remaining tasks to complete the compromise:
- Turn off “signing and sealing” to encrypt data in transit. This is easily accomplished by simply not setting the flag in the header of the MS-NRPC message.
- Change the password for the account that has been spoofed, such as for a domain controller. By using the message NetServerPasswordSet2 in MS-NRPC, they change the password for the DC by simply sending a frame with the new preferred password. Most of the time, this will just be set to a blank password.
- Login via normal processes.
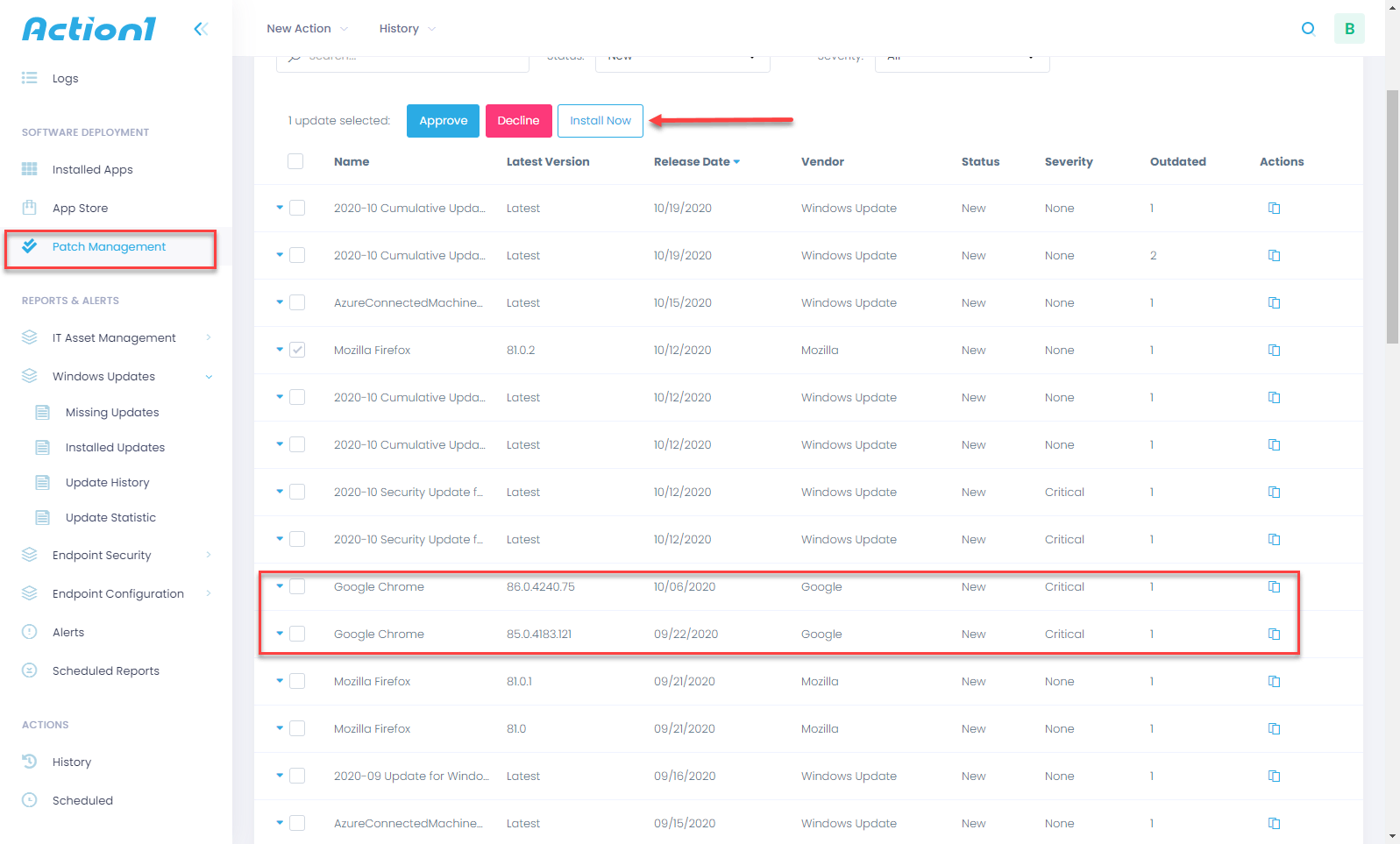
Microsoft Security Patches for Zerologon
Microsoft is addressing Zerologon in two phases, starting with the patch’s initial deployment on August 11, 2020. The phases include the following:
Phase 1
Initial deployment of the Zerologon patch to domain controllers. These patches make changes to the Netlogon protocol to protect Windows devices by default, logs connections from non-compliant devices, and enable protections for domain-joined clients.
- FullSecureChannelProtection registry key is added to domain controllers.
- Notably, a new group policy will allow non-compliant device accounts to use vulnerable Netlogon secure channel connections, even when DCs are running in enforcement mode. After the enforcement phase, those associated with the new policy will not be refused connections to the environment.
- During this phase, IT admins need to be monitoring for non-compliant connections and noting these in the event logs.
- Log event IDs 5827 and 5828 in the System event log, if connections are denied.
Phase 2
This is known as the Enforcement Phase. Starting February 9, 2021, after this date, DCs will now be in enforcement mode regardless of the enforcement mode registry key. This will start enforcing the requirement for both Windows and non-Windows devices to use the new secure RPC with Netlogon secure channel.
- Organizations can allow exceptions with the Domain Controller: Allow vulnerable Netlogon secure channel connections group policy.
Microsoft has outlined the following plan of action to address the vulnerability:
- UPDATE your Domain Controllers with an update released August 11, 2020, or later.
- FIND which devices are making vulnerable connections by monitoring event logs.
- ADDRESS non-compliant devices making vulnerable connections.
- ENABLE enforcement mode to address CVE-2020-1472 in your environment.
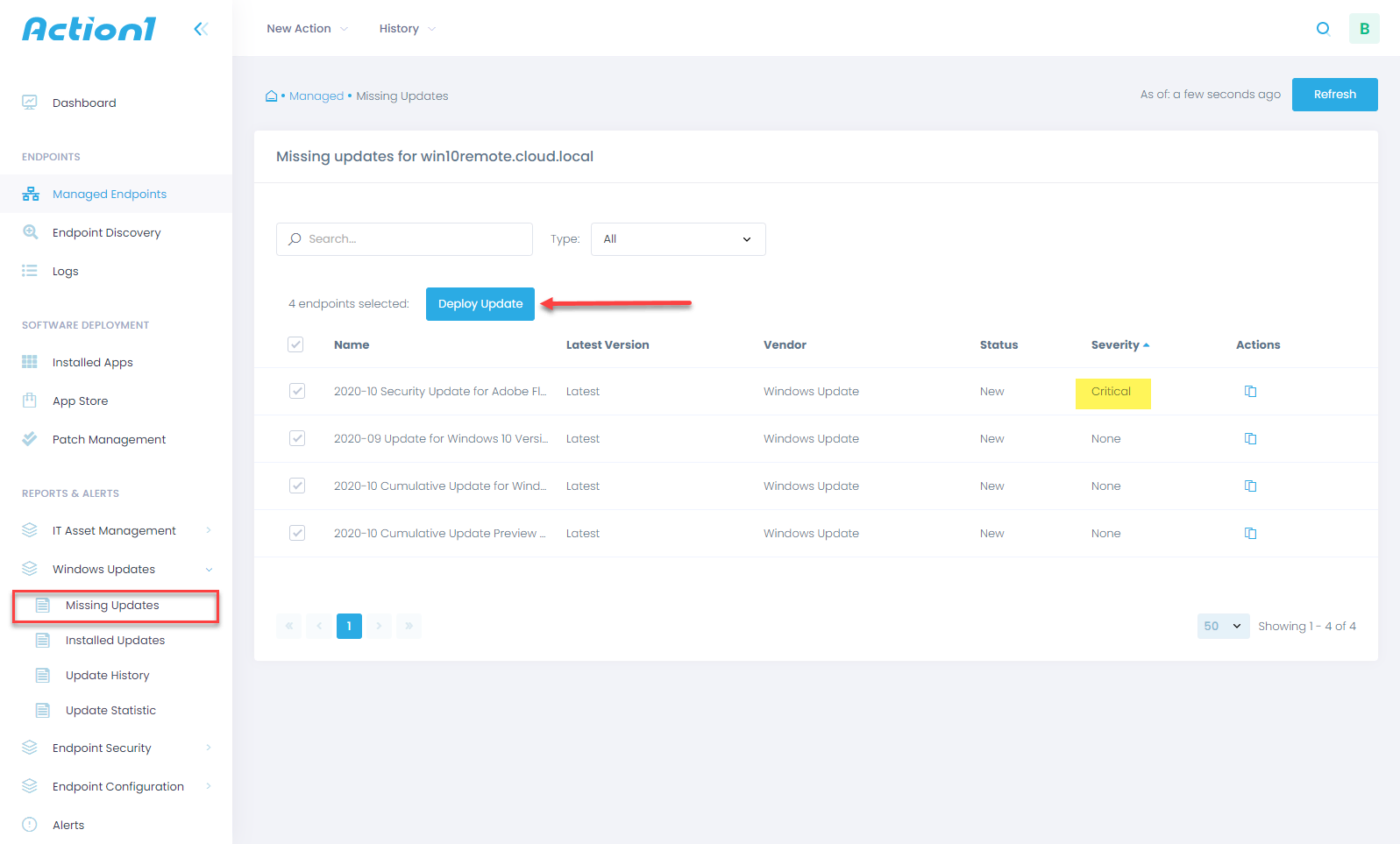
Patching Remote Windows Systems
While domain controllers are currently the recipient of the updates that adds the various functionality, Group Policy object, and registry keys to the DCs, there will no doubt be additional security updates and patches that will address various behaviors with the way clients interact with Active Directory across the board.
With the majority of employees still working remotely due to the global pandemic since the first of this year, traditional patching solutions such as Windows Server Update Services (WSUS) are no longer able to provide effective patch management to remote clients.
Action1 can also install updates for any third-party software installed on the remote client. This helps to ensure there are no vulnerabilities even from an installed software perspective.
By using cloud-based patch management, organizations can effectively keep business-critical remote systems patched effectively to help mitigate any compromise due to known vulnerabilities. Traditional patch management solutions like WSUS can no longer effectively manage Windows patching in environments where there are remote clients dispersed across numerous networks.
As the Zerologon vulnerability shows, critical vulnerabilities can expose business-critical environments and data to compromise. Cybersecurity breaches is certainly not a risk that organizations of any kind and size can take that are already challenged due to a global pandemic.
Check out Action1 here and see how it can help IT professionals to scale up IT infrastructure and optimize endpoint security effectively, manage and patch remote computers easily.