Update Rings is a powerful feature designed to simplify and improve patch management efficiency. When combined with autonomous endpoint management, it creates a mechanism for successful update deployment with minimal human intervention. This structured approach to update deployment allows organizations to test updates in controlled environments before wider rollout, significantly reducing the risk of operational disruptions caused by problematic patches while maintaining security compliance.
In this article, we will explore the insights of update rings in patch management—and answer questions like what they are, why they matter, and how to implement them effectively in your company. We will explore different ring structures (from 4-ring to 5-ring and customizable options), walk through the sequential phases of update deployment, and highlight how this approach can transform the patch management process.
Whether you are supporting a small business or a large enterprise environment, exploring update ring capabilities will help you build a more resilient, efficient, and risk-free approach to keeping your organization’s systems protected against the latest software vulnerabilities.
What are Update Rings in Patching?
Update rings in patch management allow organizations to create a deployment structure that enables testing and validating patches to see whether they work as expected before rolling them out across every endpoint in their networks.
The idea is to start with the so-called ring zero (lab environment) to verify that this set of patches is working without causing any issues, then promote them to ring 1 (pilot group of endpoints) for further validation regarding their success rates. After passing the pilot testing, organizations can deploy these patches to devices in ring 2 (larger group of endpoints). Finally, in ring 3 (broad ring), this set of updates can be rolled out across the entire network.
Why are Update Rings Important?
Update rings provide complete control over the entire process of patch deployment with the main purpose of allowing organizations to install patches across their network that work without affecting business operations through introducing unexpected failures. The staged rollout enables IT teams to detect and exclude problematic updates early that may cause application incompatibilities, performance degradation, or system crashes.
This controlled approach also allows organizations to implement deferred updates—the strategic postponement of non-critical patches according to risk-based deployment schedules—which minimizes operational disruption while maintaining appropriate security posture across different system categories. Companies with hybrid and complex environments can benefit the most from this methodical approach, due to the fact that an update that works perfectly in a lab setting might not work at all with certain software configurations or legacy systems once it is installed on pilot groups.
Furthermore, update rings enhance an organization’s security posture through faster deployment of critical patches to high-risk systems while maintaining operational stability for critical business systems, ensuring security compliance requirements without sacrificing system reliability and business continuity.
What OS and Applications Can Be Patched Using Update Rings?
You can use the update ring structure to efficiently deploy updates in Windows operating systems. Third-party applications can also be easily patched with this methodical approach. For Windows devices, update rings are particularly effective for managing feature updates, quality updates, and security patches. Microsoft incorporates this concept in their Windows Update for Business services, with Windows Update rings providing granular control through fine-tuning options that allow administrators to deploy or defer updates.
The Windows Autopatch service, primarily available for Microsoft 365 E3 and E5 enterprise licenses (with limited functionality in Business Premium), automates the update management process by intelligently delivering updates to devices based on their assigned group.
Windows Autopatch groups separate devices into four progressive deployment rings (“Test” ring at 0.5% of devices, “First” at 5%, “Fast” at 50%, and “Broad” covering the remaining 44.5%) to ensure updates are validated in smaller groups before wider deployment.
While Microsoft provides mechanisms to uninstall updates when issues are detected, this capability varies significantly by update type—feature updates can typically be rolled back within 10-30 days, while quality updates may have more limited rollback options, and some security updates cannot be cleanly uninstalled once applied without using system recovery options.
Can macOS and Linux Endpoints Use Update Rings?
While macOS doesn’t implement the “update rings” concept used by Microsoft, it does support phased deployment capabilities through MDM solutions, which allows administrators to control updates using MDM Configuration Profiles that offer flexibility to defer major OS updates up to 90 days and minor updates up to 30 days. Smart Groups in MDM solutions like Jamf Pro, Mosyle, or Kandji allow staged update deployments, which work like “update rings,” where administrators through scoped policies can control which devices will receive updates and when.
With Linux, the situation is similar. Enterprise Linux distributions support staged update deployment through repository management:
- Red Hat Enterprise Linux uses Satellite Server with Content Views to control which updates are available to different server groups.
- SUSE Linux Enterprise employs SUSE Manager with channels for staged update rollouts.
- Ubuntu offers Landscape with phased updates capabilities for controlled deployment.
Linux systems can control updates through distribution-specific mechanisms such as package pinning (Debian/Ubuntu), version locking, and repository prioritization. While not called “rings,” these mechanisms provide similar functionality for gradually deploying updates across test, staging, and production environments.
You may wonder if there’s a way to update endpoints with different operating systems from a single platform using an update ring structure. In fact, there is! By equipping your organization with patch management software that offers the update rings feature, you can manage updates for not only operating systems but also third-party applications. Such software can simplify and automate update processes, saving you time, resources, and headaches.
What are Examples of an Update Ring Structure?
The most widely implemented configurations are 4-ring and 5-ring structures, but some organizations use customized structures to meet their specific environmental complexity, compliance requirements, and risk tolerance.
Each ring represents a distinct validation phase with specific endpoints, monitoring criteria, and success metrics that must be met before progression to the next deployment stage.
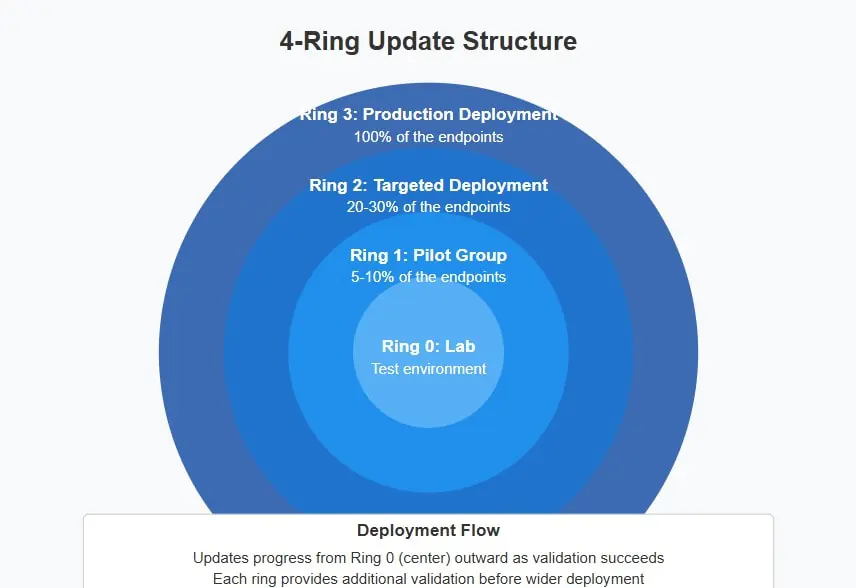
4-Ring Update Structure:
The 4-ring deployment model creates a progressive validation framework that begins with an isolated lab environment to verify the patch’s functionality. Once verified, the updates then advance to the pilot ring (5-10% of the endpoints) for validation on these devices.
The targeted deployment ring (20–30% of the endpoints) expands validation across different groups of workstations, while the final ring completes deployment for 100% of the endpoints in the organization’s network.
5-Ring Update Structure
The 5-ring structure adds an extra phase (ring) that enhances validation precision by separating critical infrastructure from standard deployment stages. The process follows a methodical progression: starting with lab environment validation, moving to pilot deployment (5-10% of endpoints), then advancing to targeted rollout (20-30% of endpoints) if specific criteria are met, followed by production deployment (60-70% of endpoints), and finally reaching critical systems in the last ring.
This approach incorporates an additional ring specifically to maximize protection for critical business systems. By ensuring patches undergo comprehensive validation before reaching systems where downtime would significantly impact business operations, organizations efficiently maintain security and operational stability across their networks.
Customizable Ring Structure
Through using advanced patch management software, organizations can customize their ring structures to adapt to specific business needs and environments through implementing deployment segments and criteria beyond percentage-based groupings. This approach offers the flexibility to create targeted deployment phases based on department functions, risk profiles, or system criticality.
For instance, smaller organizations may opt for a fewer-than-4-ring structure to simplify the process while ensuring robust protection. On the other hand, large enterprises with intricate infrastructures or specialized compliance needs can create structures with more than five rings for granular control over the process and extensive testing before rollout to their most critical systems. This flexibility of the customizable structures ensures that security measures and detailed testing of the patches are neither overburdened nor insufficient while seeking the optimal balance between operational efficiency and risk mitigation.
What do Sequential Phases Look Like in Update Rings?
We will now discuss the most widely used 4-ring update structure, providing information about each ring and what its function is.
Test Ring
The Test Ring is your lab environment where updates are tested on controlled test systems to verify functionality before being released to the workstations in the Pilot Ring.
Pilot Ring
Once the updates have been successfully tested and validated in the Test Ring, they can be deployed to a small group of endpoints in the Pilot Ring (early adopters). The Pilot Ring serves to further test updates, typically on 5-10% of the organization’s production endpoints.
Targeted Ring
After the updates have been deployed to the machines in the Pilot Ring and have not introduced any issues, they will be automatically installed to a larger group of workstations.
Broad Ring
If all of the updates work as expected, they will be deployed across every single endpoint in the organization’s network. By this stage, the updates have verified that they won’t impact endpoint stability and performance.
Action1 Update Rings Feature
Action1, a leading provider of autonomous endpoint management solutions, introduced a powerful new feature designed to make the update process more efficient, intelligent, staged, and risk-free. Organizations can now take advantage of it, ensuring only reliable and tested updates are installed throughout their networks.
Update Rings implements a staged rollout approach to patch deployment, creating sequential “rings” of devices that receive updates in phases rather than all at once. The first ring includes test systems, followed by rings of increasingly critical production endpoints. What makes this approach so effective is the real-time confidence scoring system that analyzes patch performance in each ring before allowing progression to the next.
This means that if a particular patch causes any unexpected issues in an early ring, the system automatically prevents it from moving forward and allows IT teams to manually exclude these updates from future deployment rings with just a few clicks.
The system works autonomously following predetermined rollout schedules but provides flexibility to intervene when necessary. IT teams can customize ring structures based on the organization’s specific requirements—whether extended testing is needed for business-critical systems or rapid deployment for urgent security patches. This feature is essential for SMBs and large enterprises, as it reduces downtime risks while ensuring timely remediation of critical vulnerabilities.
Using Action1’s update rings feature provides the following benefits:
- Smarter way to manage updates—Updates start in inner rings and move outward based on success metrics, which can be manually set based on your organization’s requirements.
- Less downtime, more control—Preventing problematic patches from being deployed across your entire organization’s infrastructure. If any issues arise, they will be caught in the test or pilot ring.
- Efficient autonomous patching process—Through using real-time confidence scoring, your IT team ensures only reliable updates move forward.
- Flexible scheduling capabilities—Offering the necessary flexibility to test and deploy updates at convenient times, without affecting core business operations and user experience.
- Faster remediation—Critical vulnerabilities will be addressed immediately.
How to Automate Rollout of Software Updates with Update Rings Using Action1?
To implement a typical workflow for the automated rollout of software updates, follow these steps:
Step 1. Log in or sign up to Action1.
Step 2. Navigate to the Automations tab, then click New Automation; then, select Update Ring.
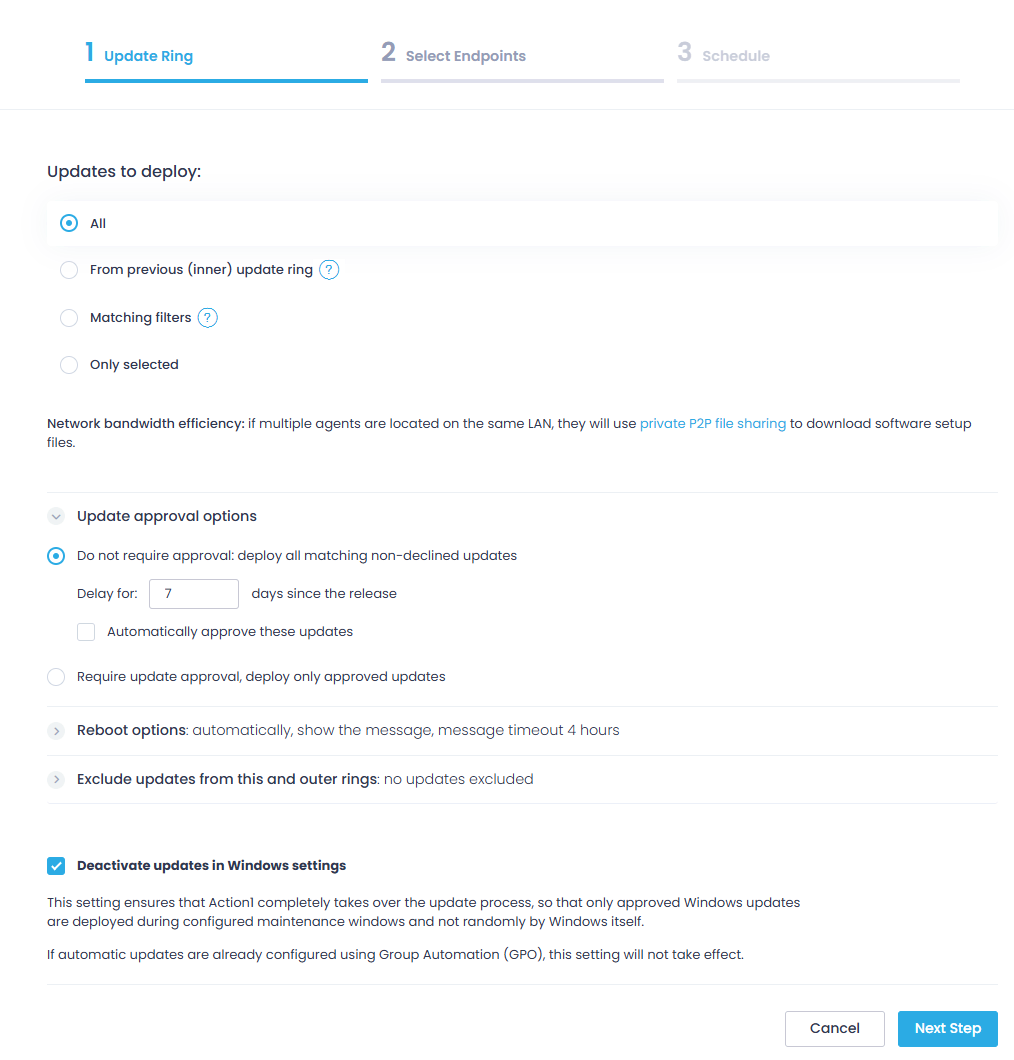
Step 3. Create Ring 0 to include the updates you want to deploy; select them from the list of currently missing updates.
The options are:
-
All—this is the default option. You can use it to install all updates, irrespective of their severity or status.
-
From the previous (inner) update ring—this option is only applicable to Ring 1, Ring 2 or Ring 3, when we already have created Ring 0. Use it to proceed with deploying non-declined and non-excluded updates from the previous ring. For example, if you are configuring Ring 1, you can deploy only the updates that were successfully validated within Ring 0.
-
Only selected—this option installs exclusively the updates you have specifically chosen from the comprehensive list of all available updates in your organization.
-
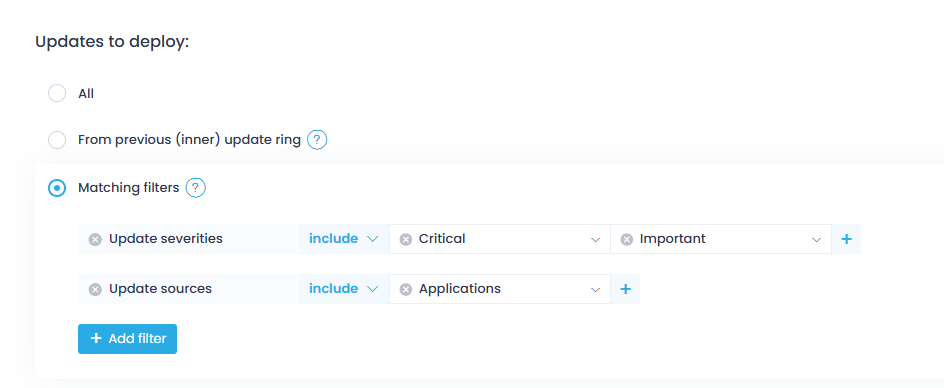
Matching filters—use this option to install the updates that match your search criteria.
→ Creating Ring 0 with matching filters:
Wondering how to configure filters?
-
Add filters such as update source, update severity, etc.
-
You can add several filters, and Action1 will search for and deploy updates that match them all at once (logical AND).
-
Within each filter, you can provide several values; Action1 will search for any of them (logical OR).
-
The values can be included or excluded. For example, search for and deploy security updates that are coming from Microsoft or Google but whose severities are anything except low.
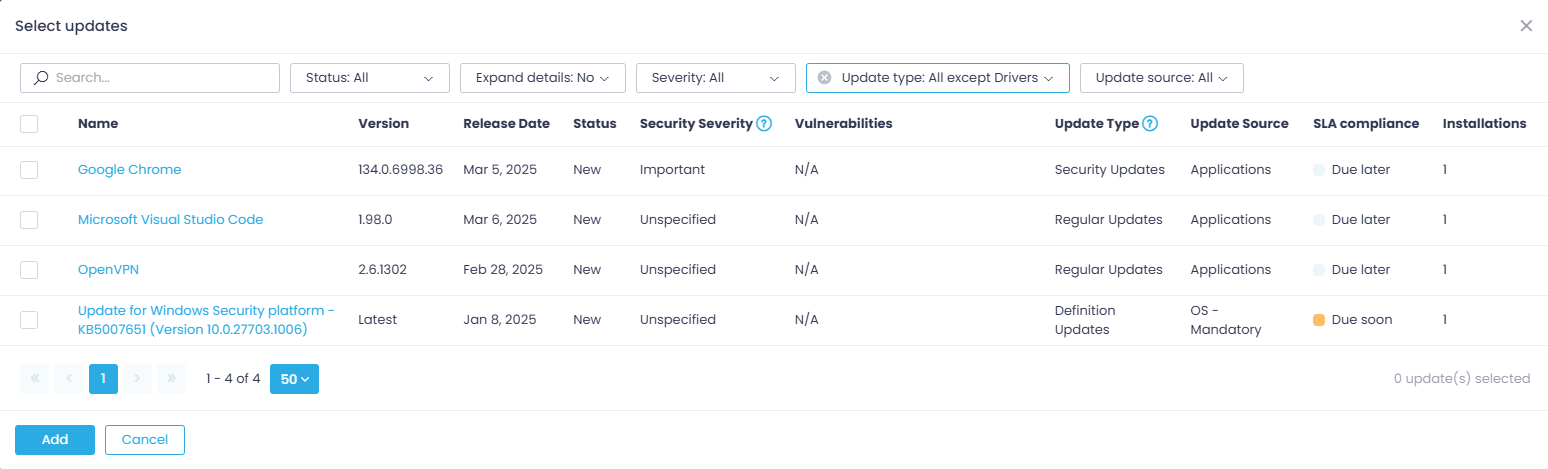
→ Creating Ring 0 with only selected updates—use this option to install specific updates you have picked from the list. It shows all available updates in the organization.
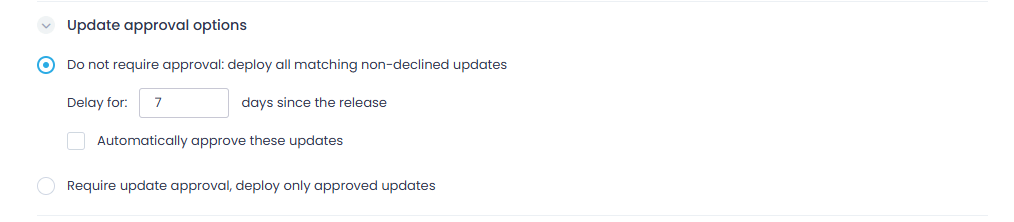
If you have selected All (first option), From previous (inner) update ring, or Matching filters, you can use Update approval options to define if you need updates to be explicitly approved before they can be scheduled for distribution.
-
Do not require approval—automatically deploy all updates that match the criteria you specified earlier and that have a status apart from Declined. Additionally, you can set the time period to wait before automatically installing the update and also to automatically change the update status to Approved.
-
Alternatively, you have the option to request update approval. If so, Action 1 will deploy only the updates that match the specified criteria and have a status of “approved.”
NOTE: Update approval options are not shown if you choose only selected —if needed, you can reach the same effect by selecting Status: Approved when putting up the list of updates.
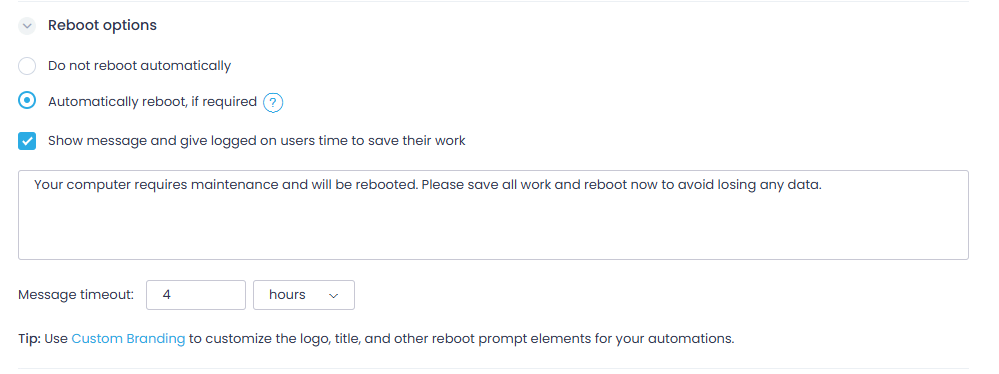
Step 6. Use Reboot options to specify whether to automatically reboot the target endpoint(s). You can also instruct Action1 to show a message to the endpoint users and give them time to save their work and set the message timeout.
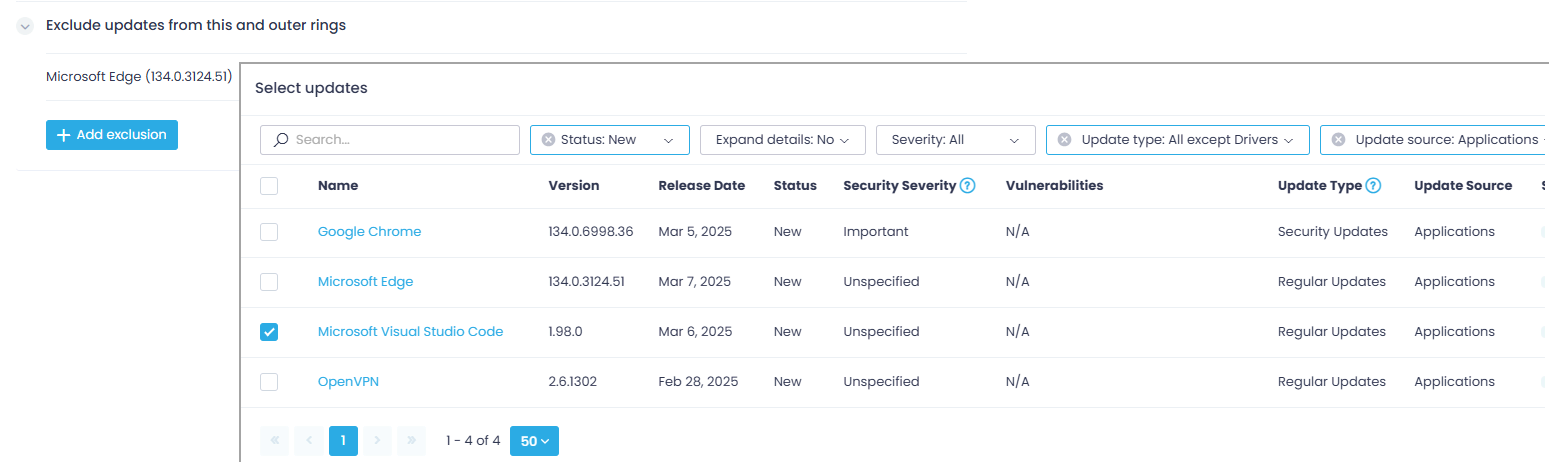
Step 7. Below the reboot options, you will find another useful drop-down menu allowing you to exclude updates from this and outer rings—from the list of available updates, select the ones you need to exclude from deployment within this ring (and, respectively, the next rings that follow).
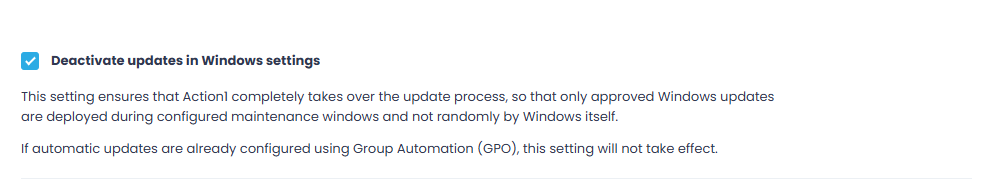
Step 8. Next, you can select to Deactivate updates in Windows settings—use it to disable Windows Update and push patches and KBs via Action1 only.
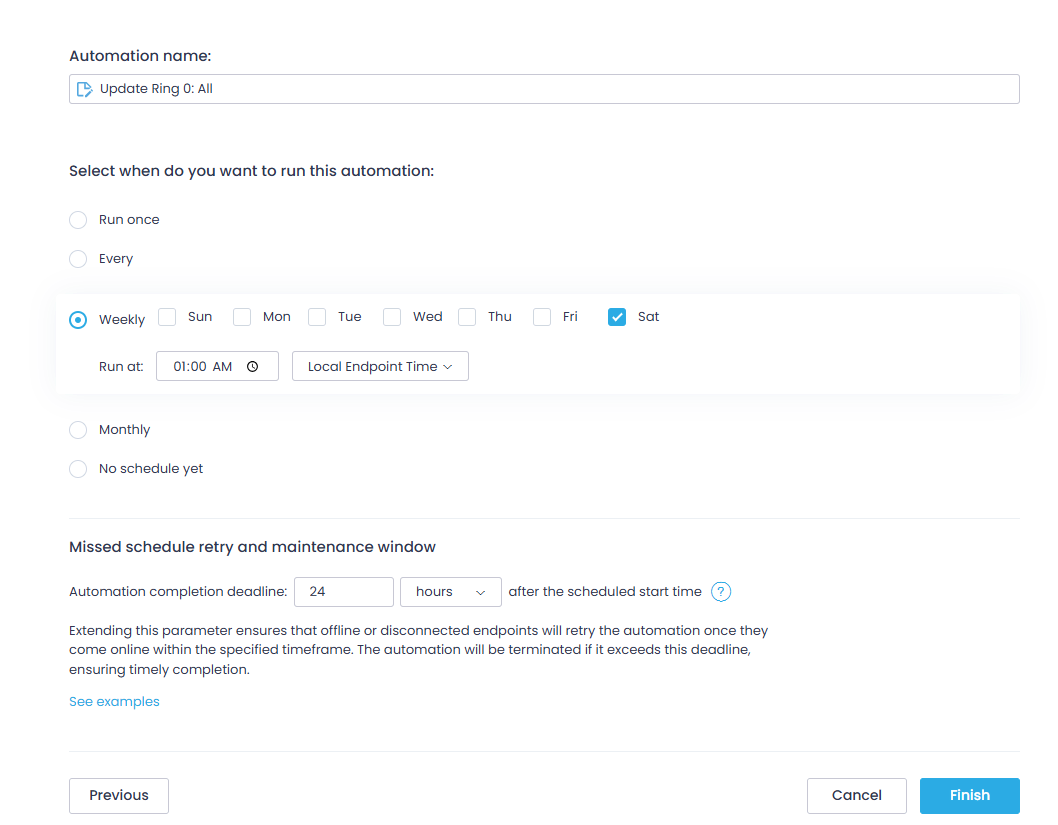
Step 9. Proceed with the next steps of the wizard to select target endpoints and configure an automation schedule based on your organization’s needs.
Keep in mind to specify the automation completion deadline after the scheduled start time. This will instruct the offline or disconnected endpoints to retry the automation once they come online within the specified timeframe.
NOTE: If you need to update this setting, make sure not to set the time frame to an interval longer than the frequency of action execution (that is, do not set it to 48 hours if the action is executed every day).
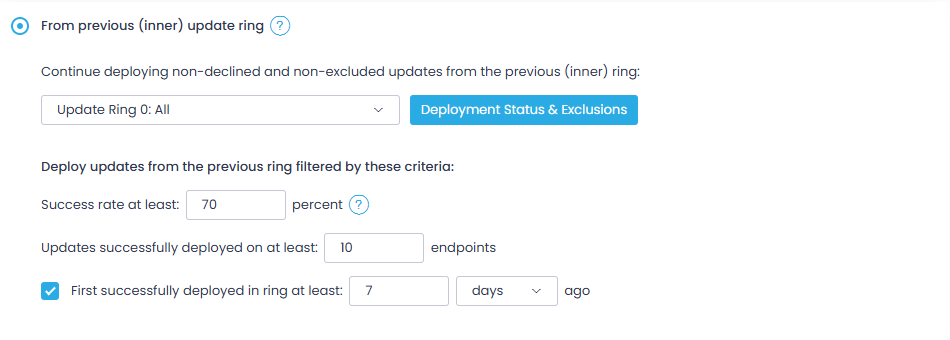
Step 10. Create Ring 1 using the From previous (inner) update ring option and selecting Ring 0 as the inner ring. Optionally, you can configure filters (e.g., success rate) to apply to the selection of updates.
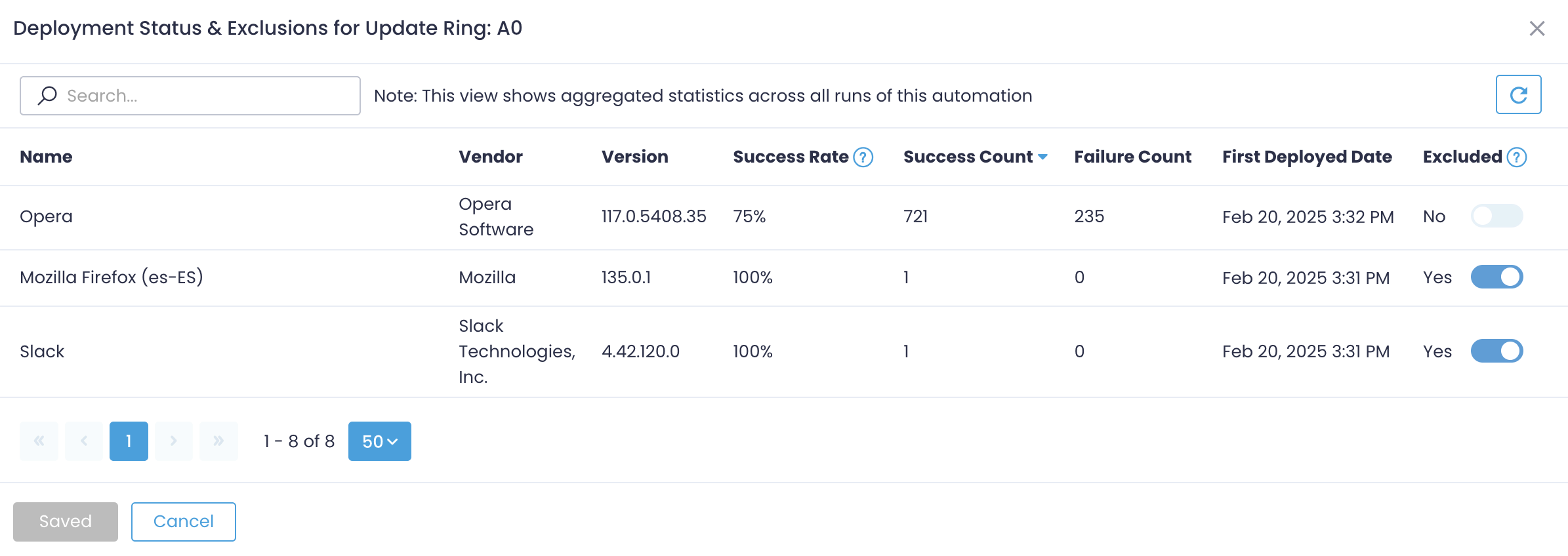
You can continue deploying non-declined and non-excluded updates from the inner ring. Click Deployment Status & Exclusions to examine the updates deployed within the selected ring.
Use the toggle switch in the Excluded field to add or remove the selected update in the exclusion list in the automation settings.
To filter the updates from the previous ring, you can configure certain criteria based on metrics (will be applied using logical AND).
Filtering criteria in detail:
-
min Success rate—the value is calculated using the following formula: Success Count / (Success Count + Failure Count) × 100
The default is 70%.
-
min Success count—number of updates successfully deployed on at least N endpoints in the inner ring (default is 10 endpoints).
-
Additionally, you can include only those that were first successfully deployed in the ring at least n days/hours/minutes ago (the default is 7 days ago).
Then continue by selecting a group of endpoints that you want to include in Ring 1 and scheduling the automation as we already did in Ring 0.
Step 11. Create all subsequent rings similarly.
Step 12. Monitor the update deployment status (by opening the Deployment Status view) for each ring.
For your further convenience, we have created a short video that walks you through the process step-by-step.