SOC 2 Compliance Patch Management Software
For Securing Customer Data on Distributed Endpoints
Automate Windows OS and third-party applications patching
Deploy and remove software across multiple endpoints
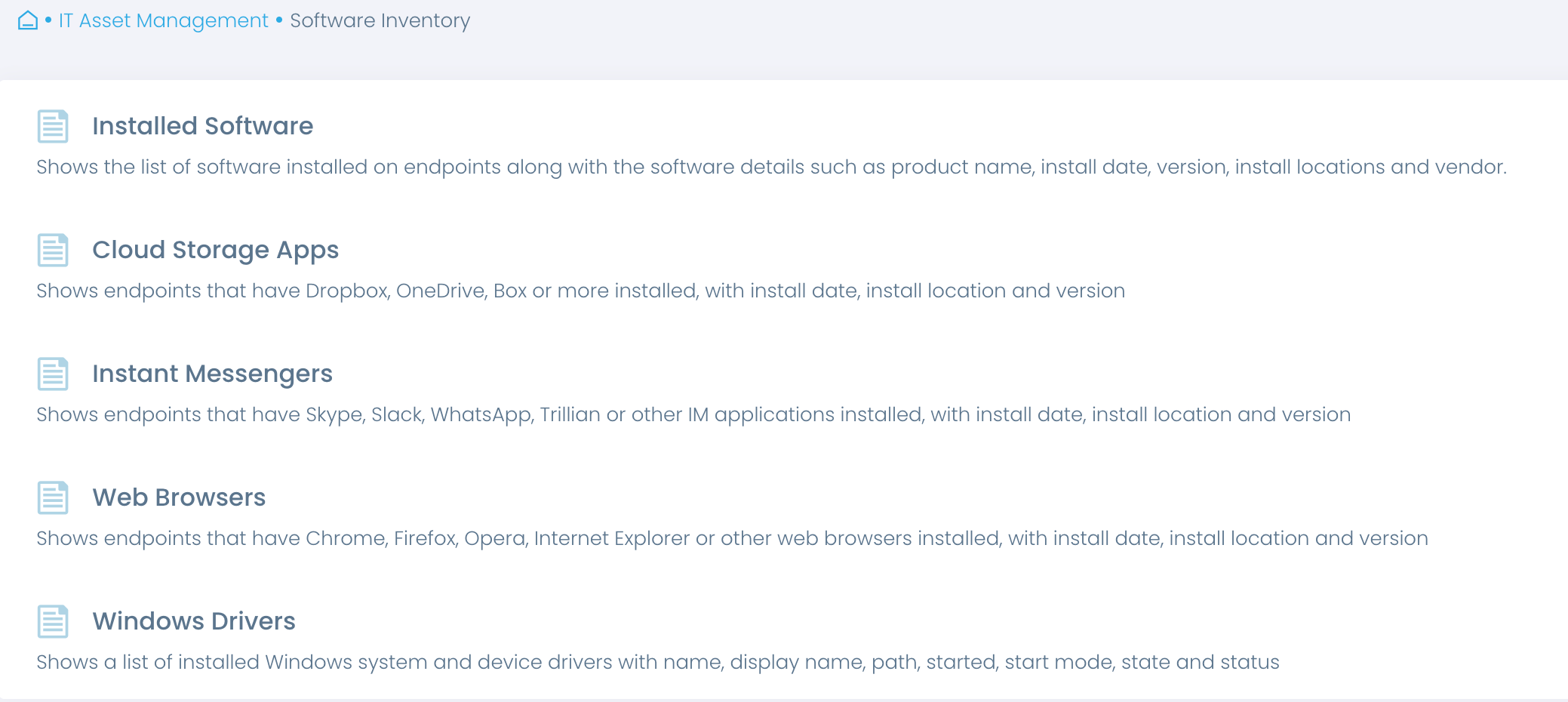
Inventory endpoint software and hardware
Enforce and maintain secure endpoint configurations
Achieve and Demonstrate SOC 2 Compliance with Action1
Unlike more detailed and specific compliance standards and frameworks, such as PCI DSS or ISO 27001, SOC 2 has no definitive controls checklist. Instead, the AICPA provides guidelines in the Trusted Services Criteria and points of focus to structure each audit and help organizations implement controls. SOC 2 software from Action1 helps you establish, maintain and demonstrate compliance with Trust Services Criteria by automating vulnerability remediation, asset inventory, software management, and endpoint configuration and monitoring.
CC3.2, CC6.1, CC6.5, CC6.8, CC7.1
Identify and manage the inventory of information assets, identify assets for disposal and prove anti-malware is in place
Maintain up-to-date asset inventory
Risk assessment and risk management start with knowing your assets. Automate asset inventory and gain accurate real-time insights into software and hardware that the business relies on. Streamline regular reviews of software and hardware in use to verify these assets are authorized, consistently applied across appropriate endpoints, and continuously updated.
Inventory information assets
Get an overview of endpoint hardware and software to make informed decisions about required replacements, upgrades and disposal, to ensure your assets remain secure and compliant.
Prove anti-malware protection
Verify and prove to auditors that your endpoints are consistently and continuously protected with authorized antivirus and anti-malware software without manual evidence collection.
Enforce approved software
Validate that no unauthorized software is installed on endpoints posing a risk to your environment and customer data. Detect unauthorized, obsolete or unsupported software to be disposed of.
CC3.2, CC5.2, CC7.4, CC7.5, CC8.1
Protect assets from external threats, identify and remediate vulnerabilities, restore the environment after an incident while managing system changes appropriately
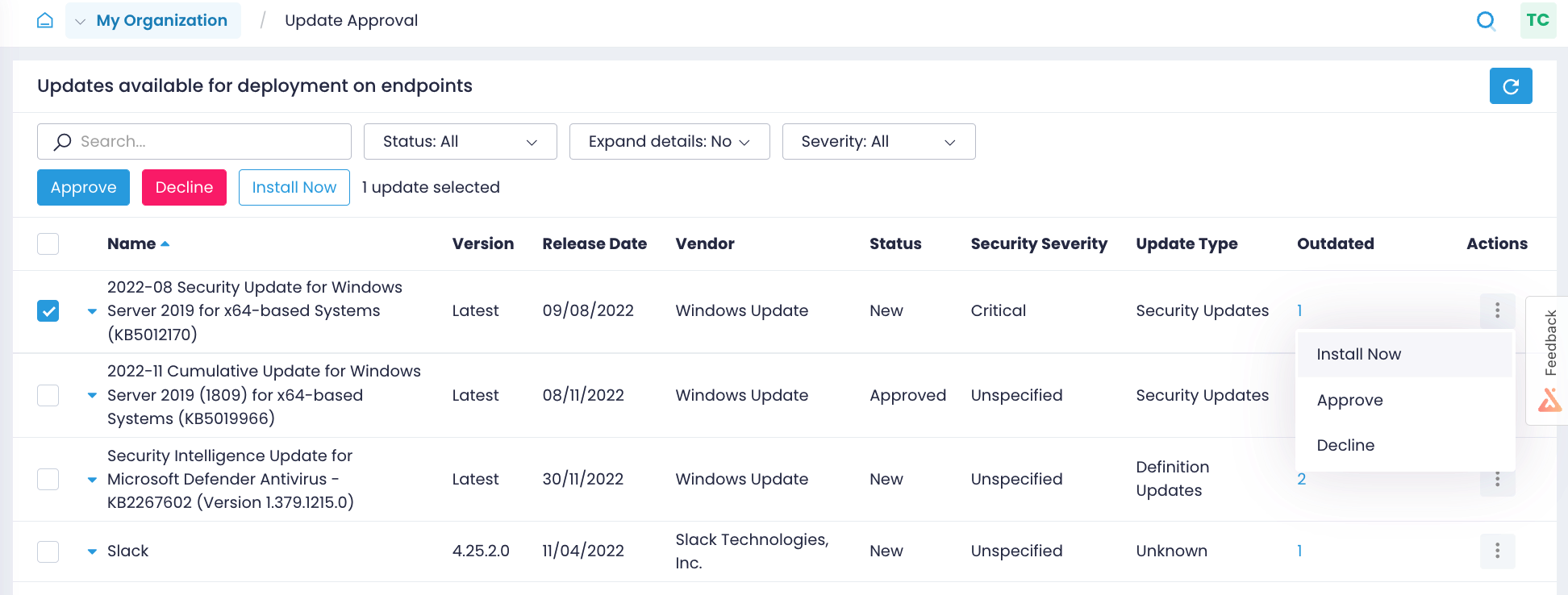
Identify and remediate vulnerabilities
Patch management is essential for achieving and maintaining SOC 2 compliance and ensuring the security and availability of an organization’s systems and data.
Keep your OS and third-party applications up to date on the latest patches with compliance automation from Action1. Patch all servers and workstations consistently even if they are remote, not connected to a corporate VPN, not joined to a domain, or offline.
Identify missing updates
Patch your Windows OS and third-party applications as soon as updates are available. Identify what patches are missing on what endpoints, and get alerts about new Windows updates.
Enable a compliant process
Test patches on isolated systems, approve updates for deployment, schedule update rollout granularly, and verify that patches were successfully applied without manually checking every workstation.
Demonstrate compliance
Prove to auditors that you have a working vulnerability remediation process in place that also follows SOC 2 change management principles with detailed reports on installed patches and patching history.
CC6.1, CC6.5, CC6.6, CC6.8
Deploy authorized software only, follow a change control process, detect unauthorized installations, and remove unused or unauthorized software
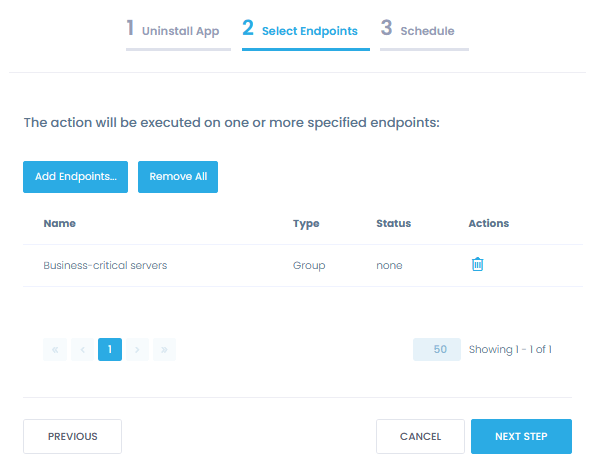
Manage software assets
Manage software lifecycle securely and more easily with compliance software from Action1. Deploy business applications and security solutions, detect unauthorized installations, and deinstall software automatically. Your endpoints don’t need to be connected to a corporate network, VPN, or joined to a domain.
Deploy authorized software
Deploy approved software, including security solutions, to any number of endpoints automatically from a single location. Keep a history of these changes to demonstrate that you follow a controlled process.
Remove unauthorized software
Discover and deinstall unapproved, unused or unsupported applications from multiple endpoints at once to bring your IT assets back to compliance. Force a reboot, if it is required to finish the process.
Detect software changes
Get real-time alerts on software changes that can bring you out of compliance, such as unauthorized software installations or the removal of an anti-malware solution from any endpoint.
CC4.1, CC5.2, CC6.1, CC6.8
Restrict access to assets, validate that controls are functioning and detect unauthorized configuration changes
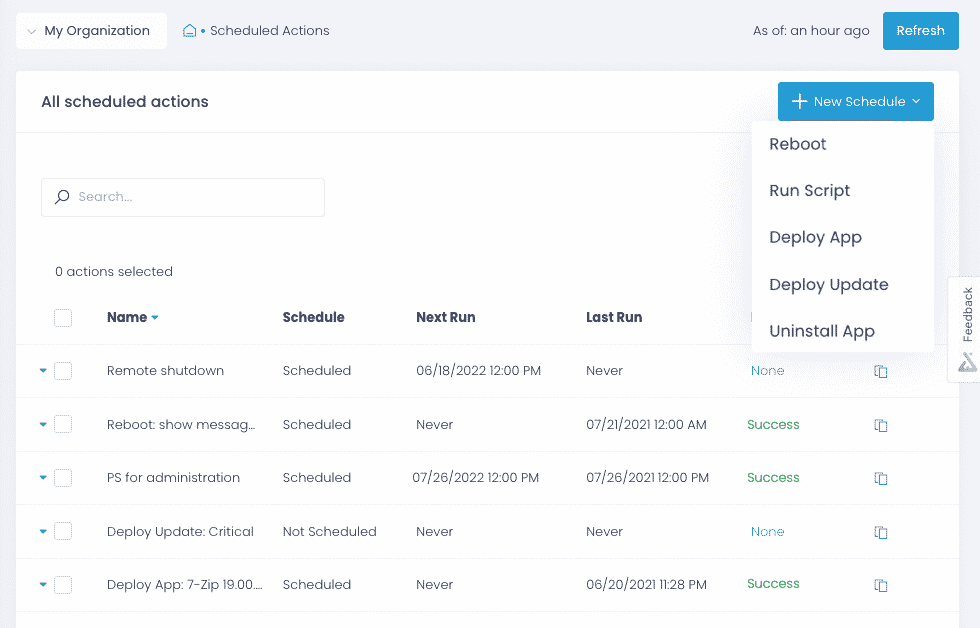
Enforce secure endpoint configurations
Apply consistent security configurations across all endpoints, including new devices and employee-owned workstations, with efficient automation and granular policy management in Action1.
Automate policy enforcement
Apply security configurations, such as enabling BitLocker and removing local admin rights, across onsite and remote endpoints with pre-built and custom scripts run automatically or ad-hoc.
Validate security controls
Support periodic evaluations with scheduled reports to ascertain that endpoint security controls are running, e.g. confirm that BitLocker is enabled and no one has unauthorized local admin rights.
Detect software changes
Get real-time alerts when someone tampers with endpoint configurations, which may indicate malicious software or an insider attack.
Security Is Our Priority
Simplify your compliance journey with a secure and compliant solution.
Security features
Action1 enforces two-factor authentication, provides role-based-access and audit logs, and secures all connections with TLS 1.2 and AES-256.
Compliant solution
Action1 is compliant with the requirements of security standards and regulations, such as SOC 2, ISO/IEC 27001 and HIPAA/HITECH.
Secure remote access
Action1 saves you from poking extra holes in your firewall configuration, such as opening an inbound port for remote connections to resources.
Trusted by many Fortune 500 companies
10M+
Managed Endpoints
3,000+
Customers
99%
Patch success rate


Why customers choose Action1
Tame complexity
Get up and running and start getting value in one hour with a solution that is easy to deploy and just works. No legacy technology, clunky tools, and feature overload.
Do it all in one place
Patch business-critical systems and applications, deploy and remove software, inventory assets, configure and monitor endpoints—all from a single centralized location.
See phenomenal ROI
What Our Customers Say
Action1 slashed times to bring our environment in line with our IT security policies from 6 hours a week to just 20 minutes a week, which is 18 times faster than with our previous approach.
With our previous tool, we were under constant risk, as 20% of our network was not being patched with security updates because they were off-site or not joined to our company domain. Action1 addresses this security gap by enabling us to establish a robust patch management program that covers 100% of our devices.
We are audited for ISO 27001:2018, and patch management is one of the requirements. Thanks to Action1, we’ve set up patching policies that meet our organization’s needs. As a result, we update the whole infrastructure in minutes. We also leverage Action1 to monitor the state of our IT assets as required by ISO 27001:2018.
Frequently asked questions
What is SOC 2 Compliant Patch Management Software?
SOC 2 Compliant Patch Management Software is a tool designed to help organizations manage software and system vulnerabilities while ensuring compliance with the Service Organization Control 2 (SOC 2) standards. SOC 2 is a compliance framework developed by the American Institute of CPAs (AICPA) that outlines criteria for managing customer data based on five “Trust Service Principles”: security, availability, processing integrity, confidentiality, and privacy.
Patch management is a critical component of SOC 2 compliance, as keeping systems up to date with security patches is essential to protecting against vulnerabilities that could jeopardize the integrity, availability, or security of customer data. SOC 2 requires organizations to demonstrate that they have strong controls in place to ensure the security and availability of their systems. This includes a formal process for identifying, evaluating, and applying patches to fix security vulnerabilities in a timely manner.
SOC 2 Compliant Patch Management Software automates the patching process, ensuring that systems remain secure and up to date. It also provides audit trails and detailed reporting to demonstrate compliance with SOC 2 requirements, allowing organizations to show that they have implemented effective controls to protect customer data and maintain service reliability.
Why is Patch Management Important for SOC 2 Compliance?
Patch management is essential for SOC 2 compliance because it directly supports the security and availability principles that underpin the SOC 2 framework. Organizations that handle sensitive customer data must demonstrate that they are taking proactive steps to secure their systems from vulnerabilities and cyberattacks. Outdated software and unpatched systems present a significant security risk, as they can be exploited by cybercriminals to gain unauthorized access to customer data or disrupt services.
SOC 2 specifically requires organizations to maintain strong security controls to protect against potential threats. Failing to apply security patches in a timely manner could result in data breaches or service outages, which would compromise the trust principles of security and availability. By implementing a robust patch management process, organizations ensure that all software, operating systems, and applications are kept up to date with the latest security fixes.
SOC 2 Compliant Patch Management Software plays a key role in automating and streamlining this process. The software continuously scans for vulnerabilities and automatically applies patches, reducing the risk of human error and ensuring that updates are consistently applied across all systems. Additionally, SOC 2 requires detailed documentation of security practices, and patch management software provides the audit logs and reporting necessary to demonstrate compliance during SOC 2 audits. This ensures that organizations can confidently prove their commitment to securing customer data and maintaining high availability.
How Does SOC 2 Compliant Patch Management Software Improve Security?
SOC 2 Compliant Patch Management Software significantly improves security by automating the identification, deployment, and monitoring of patches across an organization’s infrastructure. By keeping systems up to date with the latest security patches, the software helps protect against vulnerabilities that could be exploited by cyberattacks, such as data breaches, malware infections, and ransomware.
In the context of SOC 2, security is one of the core trust principles, and it requires organizations to demonstrate that they have implemented effective measures to prevent unauthorized access to systems and data. Unpatched vulnerabilities in software can provide an entry point for hackers, making patch management an essential aspect of maintaining security. SOC 2 Compliant Patch Management Software ensures that all systems, including servers, databases, applications, and endpoints, are consistently updated, reducing the risk of a security breach.
In addition to automating the patching process, this software also provides detailed visibility into the patch status of all systems. IT teams can quickly identify systems that are out of compliance or require urgent updates, minimizing the window of exposure to potential attacks. The software generates audit-ready reports that show when and where patches were applied, which is crucial for SOC 2 compliance.
Moreover, automating patch management reduces the risk of human error, ensuring that patches are applied consistently across the organization. It also frees up IT resources, allowing security teams to focus on other critical aspects of maintaining a secure environment. In summary, SOC 2 Compliant Patch Management Software helps organizations safeguard customer data, maintain compliance, and build trust with clients by securing their systems against vulnerabilities.
Who has to comply with SOC 2?
SOC 2 is designed for organizations that provide services and host data on behalf of other companies, such as cloud service providers, managed service providers, and software-as-a-service (SaaS) companies. These organizations must undergo an audit by a third-party assessor to ensure that they meet the security and availability standards set forth in the SOC 2 framework. Once the audit is complete, the organization will receive a report, which can be shared with potential customers to demonstrate the organization’s commitment to security and availability.
What are SOC 2 cybersecurity requirements?
Security requirements are the only ones that are not optional under SOC 2. It has a number of specific requirements for security, including:
- Developing and implementing written policies and procedures for security and availability.
- Protecting the confidentiality, integrity, and availability of information.
- Regularly testing and monitoring security controls to ensure they are operating effectively.
- Implementing access controls to prevent unauthorized access to systems and data.
- Protecting against malware and other types of security threats.
- Regularly performing backups and disaster recovery procedures to ensure the availability of systems and data.
Overall, SOC 2 requires organizations to take a comprehensive approach to cybersecurity, with a focus on protecting their systems and data from a wide range of threats.