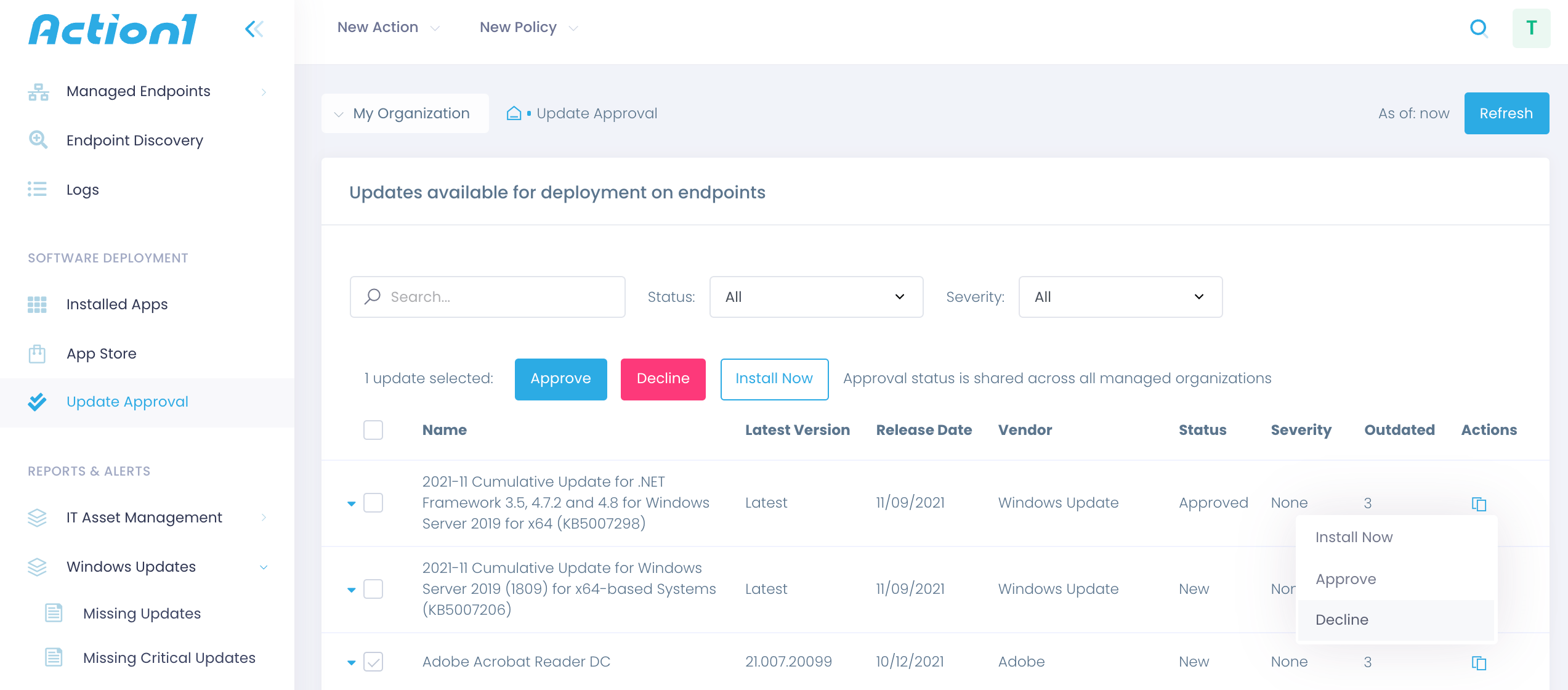
Decline Patches
Meticulously assessing each software patch and Window KB before attempting delivery is crucial for successful patch management and IT governance. Action1 recommends testing patches on a smaller group of computers before scheduling a companywide rollout. While in most cases, patches seamlessly integrate with your current apps and OS, every so often system administrators have to sacrifice the most recent updates for the sake of system integrity and operability.
When does it make sense to decline patches?
- A patch is known to cause compatibility issues
- A patch is known to compromise the system security
- A patch needs extensive testing
- A patch violates compliance standards and regulations
- A patch may arise license issues with legacy apps
- A patch is irrelevant or optional
How to review and decline updates?
Action1 enables you to assess patches before distribution. The Update Approval dashboard lists all pending third-party patches and Windows updates. Before a review, all patches are assigned the New status. Once you review and test a hotfix (for example, by installing it to a small group of test endpoints), select Actions and either approve or decline a patch.
Filtering out updates by their status helps you discover declined patches.
What does excluding updates entail?
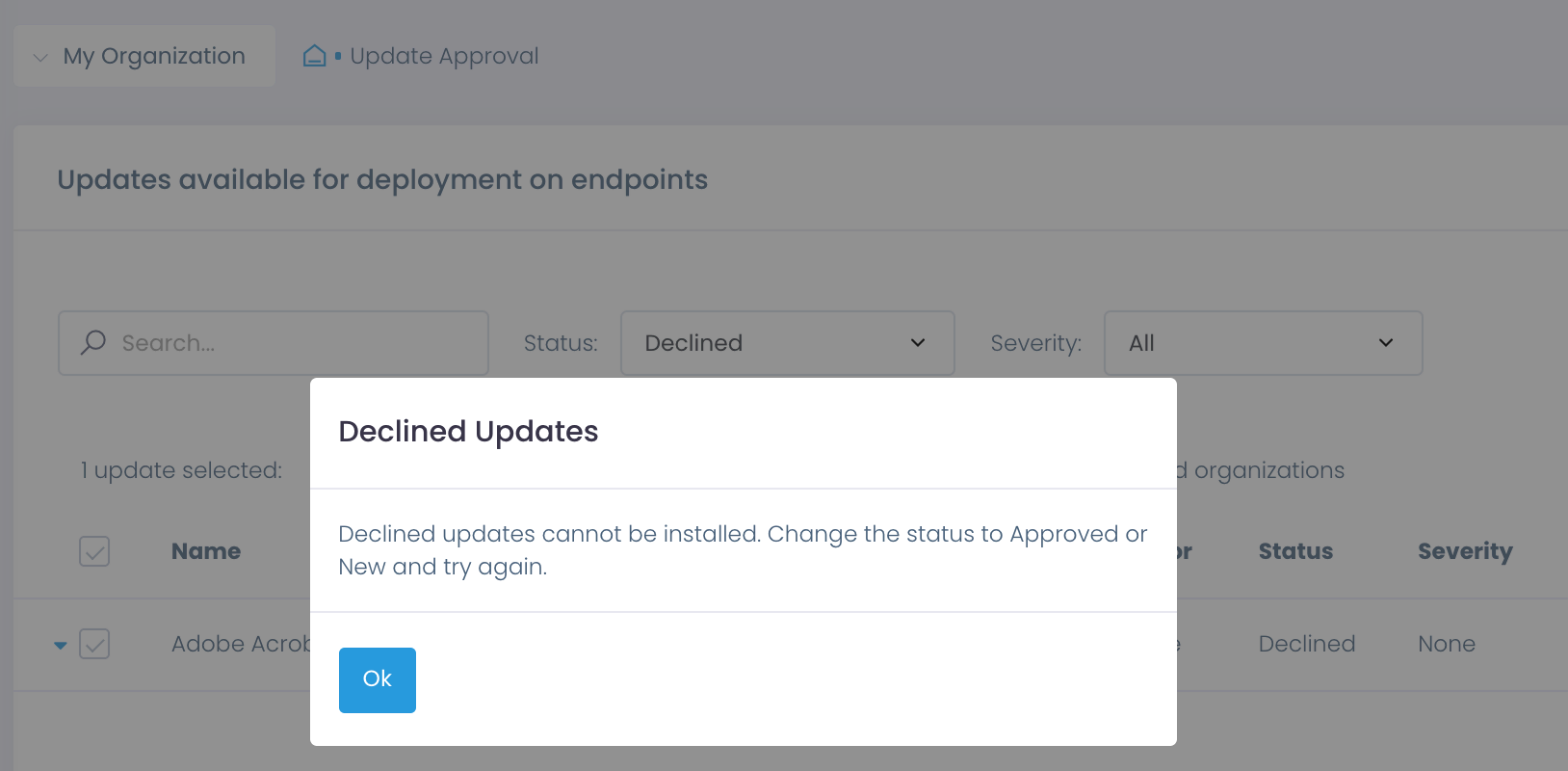
Declining problematic patches is a step of the patch management procedure that safeguards your system and makes it accountable. By marking the patch declined, you attest that the patch has been reviewed and hasn’t passed your quality gate. Action1 restrains you from occasionally installing a declined patch while still keeping its details in the system. Such patches can be eventually installed after extensive testing and approval sign-off — be sure to change its status to New or Approved before attempting a new rollout.
Patch Management That Just Works
to prevent security breaches and ransomware attacks.