Cloud-Native HIPAA Compliance Patch Management Software
For Securing Health Data on Distributed Endpoints
Patch Windows OS and third-party applications
Deploy security software to remote workstations
Inventory endpoint software and hardware
Enforce and maintain secure endpoint configurations
How Action1 Helps with HIPAA Requirements for patching endpoints
45 C.F.R. § 164.308(a)(1)(ii)(A),
45 C.F.R. § 164.308(a)(1)(ii)(B)
The HIPAA Security Rule requires covered entities and business associates to conduct a risk assessment and mitigate vulnerabilities that threaten the security of electronic protected health information (ePHI). This includes identifying and mitigating risks unpatched software poses to an organization’s ePHI.
Remediate vulnerabilities
Implement an OCR-recommended, HIPAA-compliant patch management process from end to end, and demonstrate to auditors that you have it in place. Check this box on your compliance checklist confidently and with ease.
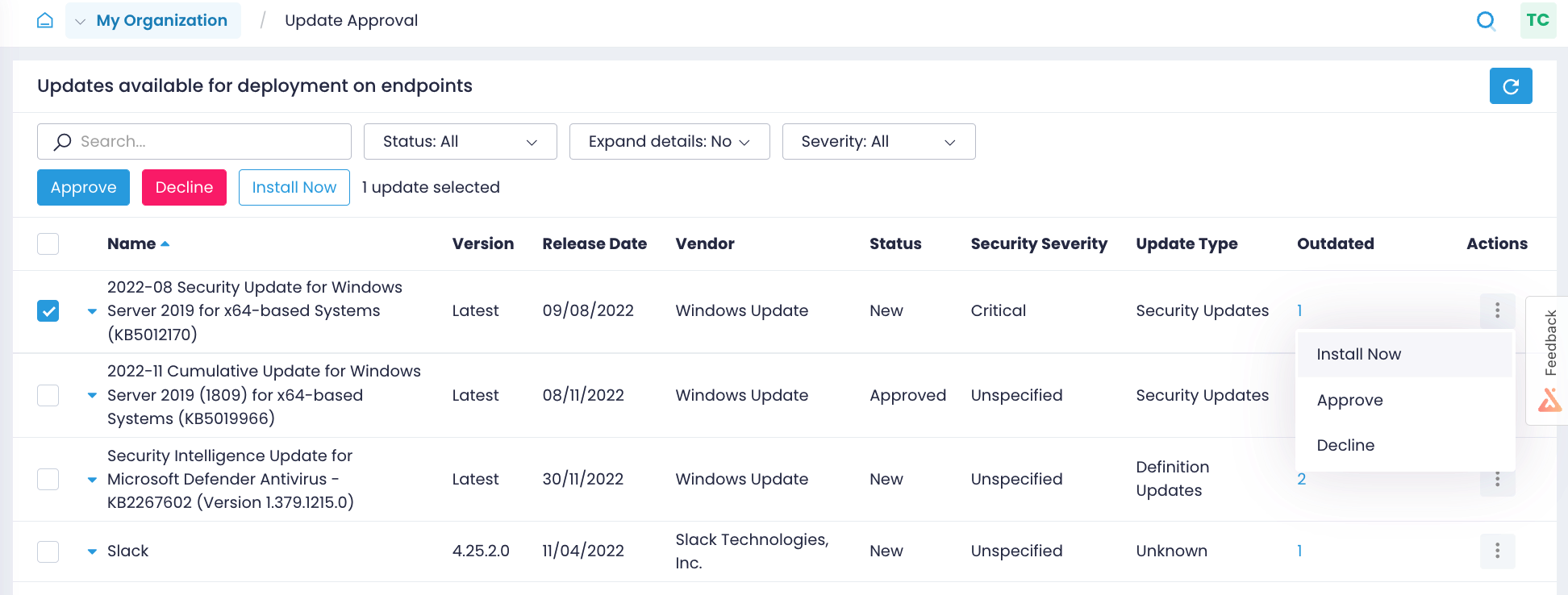
Keep your OS and third-party applications, including your custom and proprietary software, up to date on the latest patches. Patch all servers and workstations even if they are remote, not connected to a corporate VPN, not joined to a domain, or offline.
Identify missing updates
Close the window of opportunity for attackers by identifying what Windows OS and third-party application updates are missing on what endpoints and getting alerts on new Windows updates.
Automate patching
Test patches on isolated systems before their rollout, approve updates for deployment, and schedule updates to be applied to production systems as granularly as you need.
Verify patching results
Validate in real time that patches were applied correctly without manually checking every workstation. Get reports on installed updates to prove your HIPAA compliance to auditors.
45 C.F.R. § 164.308(a)(1)(ii)(A)
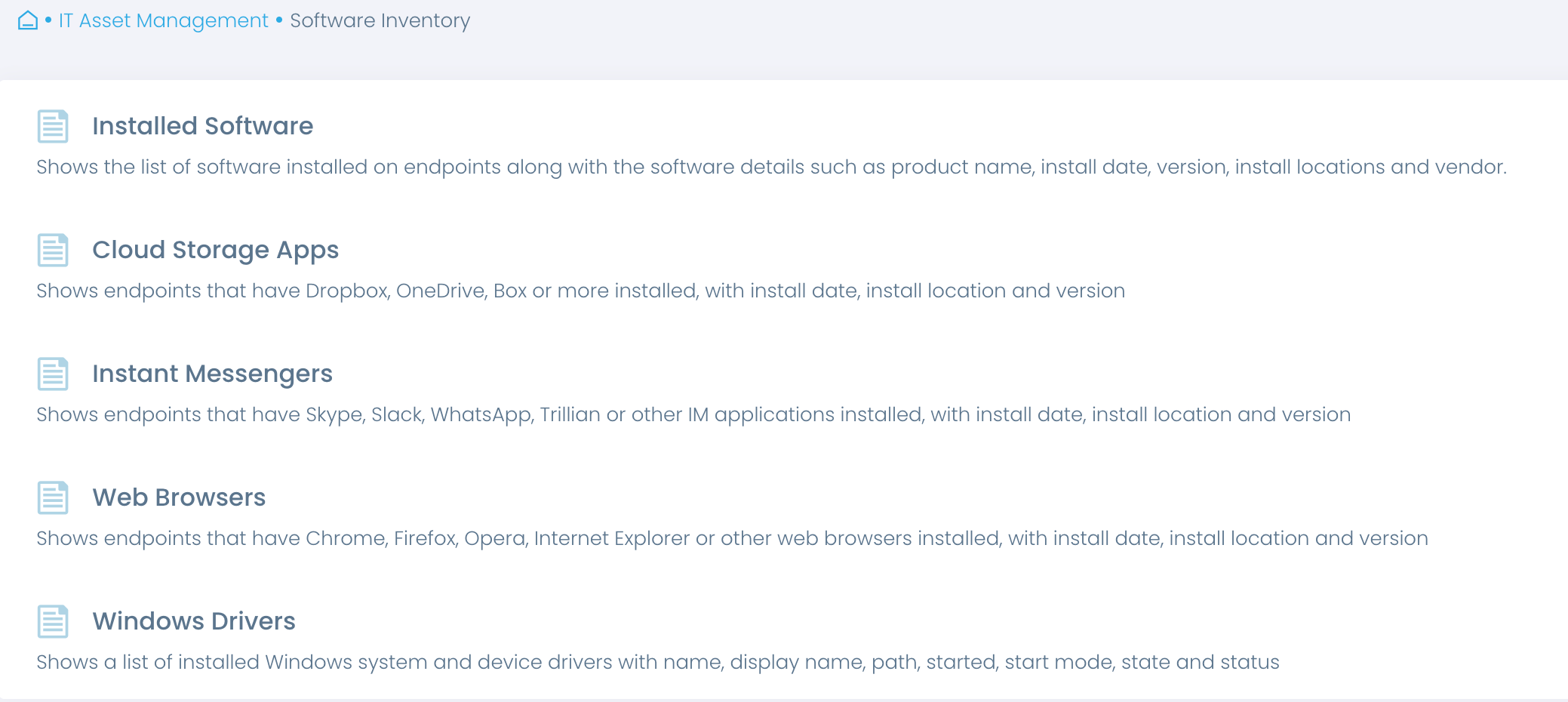
As directed by OCR, covered entities should have an inventory of operating systems, applications, device firmware, and other software. It helps healthcare providers determine which patches they need to apply.
Keep up-to-date asset inventory
Start your risk management with an automated inventory. Gain accurate real-time insights into software in use, including its versions, installation dates and more, and verify that these systems and applications continue to be updated.
Verify that no unauthorized software is installed on endpoints. Automate the removal of unauthorized or unsupported software to strengthen your data security.
45 C.F.R. § 164.308(a)(5)(ii)(B)
HIPAA standards require covered entities to use anti-malware to prevent a data breach.
Deploy and update anti-malware
Ensure and demonstrate to auditors that your servers and workstations are protected with authorized and up-to-date anti-malware.
Deploy Webroot, Malwarebytes, or other security and HIPAA compliance solutions consistently across all onsite and remote endpoints and update it as soon as a new update is available from a single centralized location. Be notified about any removal of an anti-malware solution that can bring you out of compliance.
45 C.F.R. § 164.308(a)(6)
HIPAA requires a covered entity or business associate to identify and respond to security incidents.
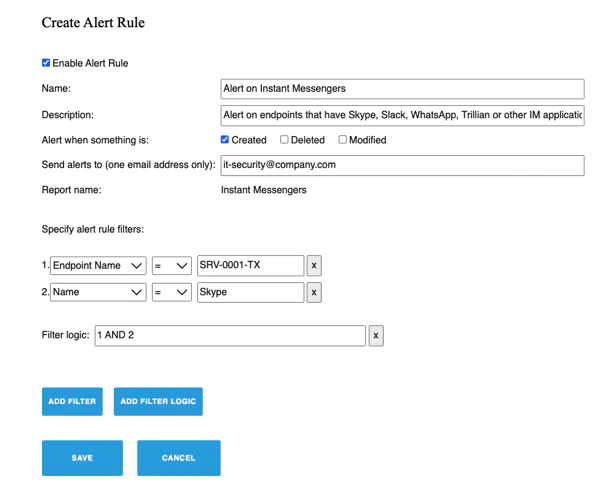
Detect and respond to incidents faster
Get real-time alerts on security changes on your endpoints that may result in a breach, such as unauthorized software installations, encryption disabled or unauthorized accounts created.
Respond to incidents faster and bring your endpoints back to a secure state with automated actions applied to individual machines or in masse.
45 C.F.R. § 164.312(a)(2)(iii)
45 C.F.R. § 164.312(a)(2)(iv)
Covered entities and business associates must implement technical controls to ensure that only personnel with authorized access rights can access ePHI.
Enforce secure endpoint configurations
Apply security configurations, such as enforcing automatic logoffs and enabling BitLocker, across onsite and remote endpoints with pre-built and custom scripts without manually connecting to individual machines.
Verify that your technical safeguards for endpoints are in place with pre-built and custom reports, e.g. that BitLocker is enabled and workstations are protected with HIPAA-compliant encryption.
Security Is Our Priority
Action1 helps healthcare providers fulfill HIPAA requirements and OCR guidelines on patch management and endpoint security configurations and is also a secure and compliant solution.
Security features
Action1 enforces two-factor authentication, provides role-based-access and audit logs, and secures all connections with TLS 1.2 and AES-256.
Compliant solution
Action1 is compliant with the requirements of security standards and regulations, such as SOC 2, ISO/IEC 27001 and HIPAA/HITECH.
Secure remote access
Action1 saves you from poking extra holes in your firewall configuration, such as opening an inbound port for remote connections to resources.
Trusted by many Fortune 500 companies
10M+
Managed Endpoints
3,000+
Customers
99%
Patch success rate


Why customers choose Action1
Tame complexity
Get up and running and start getting value in one hour with a solution that is easy to deploy and just works. No legacy technology, clunky tools, and feature overload.
Stay flexible
Implement patch management, inventory, endpoint security, and monitoring requirements the way your organization needs, with granular, easily customizable policies.
See phenomenal ROI
What Our Customers Say
Without adequate patch management in place, I would have to go around to each individual machine to keep them updated. It could leave us open to security vulnerabilities, as a manual approach always leaves a gap for patches to be missed
With our previous tool, we were under constant risk, as 20% of our network was not being patched with security updates because they were off-site or not joined to our company domain. Action1 addresses this security gap by enabling us to establish a robust patch management program that covers 100% of our devices.
We are audited for ISO 27001:2018, and patch management is one of the requirements. Thanks to Action1, we’ve set up patching policies that meet our organization’s needs. As a result, we update the whole infrastructure in minutes. We also leverage Action1 to monitor the state of our IT assets as required by ISO 27001:2018.
Frequently Asked Questions
What is HIPAA compliance?
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law that was enacted in 1996. It sets forth rules and regulations designed to protect the security and privacy of personal health information. To be HIPAA-compliant, an organization must take steps to ensure that it is protecting the confidentiality, integrity, and availability of personal health information. This involves implementing certain policies and procedures, training staff on HIPAA requirements, and regularly monitoring the organization’s compliance with the law.
Is HIPAA compliance required?
Yes. All individuals and organizations that handle personal health information, must be HIPAA-compliant. Violations of HIPAA can result in fines and other penalties.
Who does HIPAA apply to?
HIPAA applies to a wide range of organizations and individuals known as “covered entities.” This includes healthcare providers, such as doctors and hospitals, health plans, such as insurance companies, and healthcare clearinghouses, which process health information. HIPAA also applies to certain “business associates” of covered entities, such as companies that provide billing or transcription services to a hospital. HIPAA applies to any individual or organization that handles personal health information, regardless of whether they are located in the United States.
How to get HIPAA compliance?
Here are some specific steps that an organization can take to become HIPAA-compliant:
-
- Conduct a thorough risk assessment to identify potential vulnerabilities in the organization’s handling of personal health information.
- Develop and implement policies and procedures that are designed to protect personal health information, including policies on access control, data security, and data disposal.
- Train all staff on HIPAA requirements and the organization’s policies and procedures.
- Implement technical safeguards, such as encryption and firewalls, to protect personal health information.
- Regularly monitor and audit the organization’s compliance with HIPAA requirements.
- Work with legal and compliance experts to ensure that the organization meets all HIPAA obligations.
- Develop a plan for responding to HIPAA violations and breaches of personal health information.
It is important for organizations to consult with legal and compliance experts to develop a plan that meets their specific needs.
How much does HIPAA compliance cost?
It is difficult to estimate the cost of HIPAA compliance, as it can vary depending on the type, size and complexity of the organization. In general, smaller organizations may be able to implement HIPAA-compliant policies and procedures at a lower cost than larger organizations. Experts estimate that ballpark numbers are $4,000 – $12,000 for a small covered entity and $50,000+ for a medium to large business. Additionally, organizations may need to invest in technology and other tools to help them comply with HIPAA requirements.
What are the benefits of HIPAA compliance software?
HIPAA compliance software helps healthcare organizations improve security and protect personal health information. By using HIPAA compliance software, organizations also reduce their risk of HIPAA violations and breaches of personal health information. This can help to protect the organization from financial penalties and reputational damage. Additionally, HIPAA compliance software enables healthcare organizations to reduce time and effort spent achieving and maintaining compliance so they can focus on improving individuals’ and communities’ health and wellbeing.
What is HIPAA Compliant Patch Management Software?
HIPAA Compliant Patch Management Software is a tool designed to ensure that organizations in the healthcare sector maintain up-to-date software by applying necessary security patches, all while meeting the stringent privacy and security standards set by the Health Insurance Portability and Accountability Act (HIPAA). HIPAA regulations require that healthcare organizations safeguard electronic Protected Health Information (ePHI) from unauthorized access, use, or disclosure. Failing to apply patches to systems can leave software vulnerable to cyberattacks, which may result in data breaches that compromise sensitive patient information.
Patch management software automates the process of detecting, evaluating, and deploying patches across various systems and devices, such as operating systems, medical devices, and software applications. HIPAA-compliant solutions provide enhanced features, such as detailed audit trails, encryption, and compliance reporting, which are vital for meeting HIPAA’s administrative, physical, and technical safeguard requirements.
By integrating this type of software, healthcare organizations can minimize their risk of cyberattacks and ensure they remain in compliance with HIPAA regulations. This is critical not only for protecting patient privacy but also for avoiding substantial fines and legal consequences associated with non-compliance.
Why is Patch Management Important for HIPAA Compliance?
Patch management plays a crucial role in HIPAA compliance because it directly impacts the security of electronic Protected Health Information (ePHI). One of the most significant threats to healthcare organizations is the vulnerability of unpatched software, which can be exploited by cybercriminals to gain unauthorized access to sensitive patient data. As per HIPAA’s Security Rule, organizations must implement technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Unpatched systems are a primary target for cyberattacks like ransomware, malware, and phishing. These types of attacks can result in unauthorized access to ePHI, leading to data breaches, which could expose patient information and damage a healthcare organization’s reputation. Moreover, failure to secure systems could result in hefty penalties under HIPAA, with fines reaching as much as $1.5 million per violation category, depending on the severity of non-compliance.
Proper patch management ensures that all systems are up-to-date with the latest security fixes, reducing the risk of exploitation. HIPAA-compliant patch management software helps automate and monitor the patching process while ensuring that detailed records are kept, allowing organizations to demonstrate their commitment to maintaining secure systems. These records are essential for compliance audits and for proving that an organization has taken appropriate steps to protect patient information.
How Does HIPAA-Compliant Patch Management Software Help Mitigate Security Risks?
HIPAA-compliant patch management software is an essential tool for mitigating security risks in healthcare organizations, particularly in protecting ePHI from unauthorized access and cyberattacks. This software helps healthcare IT teams stay ahead of vulnerabilities by automatically identifying, testing, and deploying critical patches across networks and devices. Keeping systems up to date with the latest security patches reduces the attack surface that hackers might exploit.
One of the core security risks in healthcare IT systems is the reliance on multiple devices and platforms, from desktops to medical devices, all of which may require regular updates. A single unpatched device or software could expose the entire network to vulnerabilities, leading to potential breaches of ePHI. HIPAA-compliant patch management software centralizes the management of these patches, ensuring uniform security across all devices.
Additionally, this software often comes with compliance-specific features, such as robust reporting and audit logs, enabling healthcare organizations to document patching activities and demonstrate their compliance with HIPAA’s technical safeguard requirements. This is crucial in the event of a breach or audit, as organizations need to show that they have taken reasonable steps to protect patient data.
By reducing manual patching tasks, the software minimizes human error and ensures that updates are applied on time, significantly lowering the risk of attacks like ransomware, which has been a growing concern in the healthcare sector. In summary, HIPAA-compliant patch management software provides healthcare organizations with the tools to secure their IT infrastructure and protect sensitive health information.
What Features Should You Look for in HIPAA Compliant Patch Management Software?
When choosing HIPAA-compliant patch management software, several key features should be considered to ensure that it meets both security needs and regulatory requirements. First and foremost, the software must have strong encryption protocols to protect the transmission and storage of patch-related data, ensuring that sensitive information is not exposed during the patching process.
Another essential feature is detailed logging and audit trails. HIPAA mandates that healthcare organizations must be able to provide evidence of their security measures. Patch management software should record every action taken, including when patches were applied, which systems were updated, and who authorized the patching. This helps demonstrate compliance during an audit and ensures accountability within the IT team.
Automation is also a critical feature. Manual patch management is time-consuming and prone to errors, making it harder to maintain HIPAA compliance. Automated software can continuously monitor for vulnerabilities, apply patches across various systems, and generate compliance reports, freeing up IT resources for other critical tasks. Additionally, the software should support a wide range of systems, including operating systems, third-party applications, and medical devices.
Compliance-specific reporting capabilities are another must-have. The software should be able to generate comprehensive reports tailored to HIPAA compliance, which can be used to demonstrate adherence to security protocols in the event of an audit.