GLBA/FFIEC Compliance Patch Management Software
For Securing Customer Data on Distributed Endpoints
Patch Windows OS and third-party applications
Automate inventory of endpoint software and hardware
Enforce and maintain secure endpoint configurations
Deploy authorized software and remove unauthorized one
FFIEC Information Security Controls Action1 Helps With
While the Gramm-Leach-Bliley Act (GLBA) mandates that financial institutions protect their customers’ personal and financial information, it is the Federal Financial Institutions Examination Council (FFIEC) that provides guidance on the implementation of GLBA and develops standards for the examination and supervision of financial institutions. The following mapping of Action1 capabilities to GLBA/FFIEC requirements is based on the “Information Security Booklet” which, among other booklets, constitutes the FFIEC Information Technology Examination Handbook (IT Handbook) designed to help financial institutions understand and comply with GLBA.
II.C.10(d); II.C.10(b); II.C.15(d); IV.A
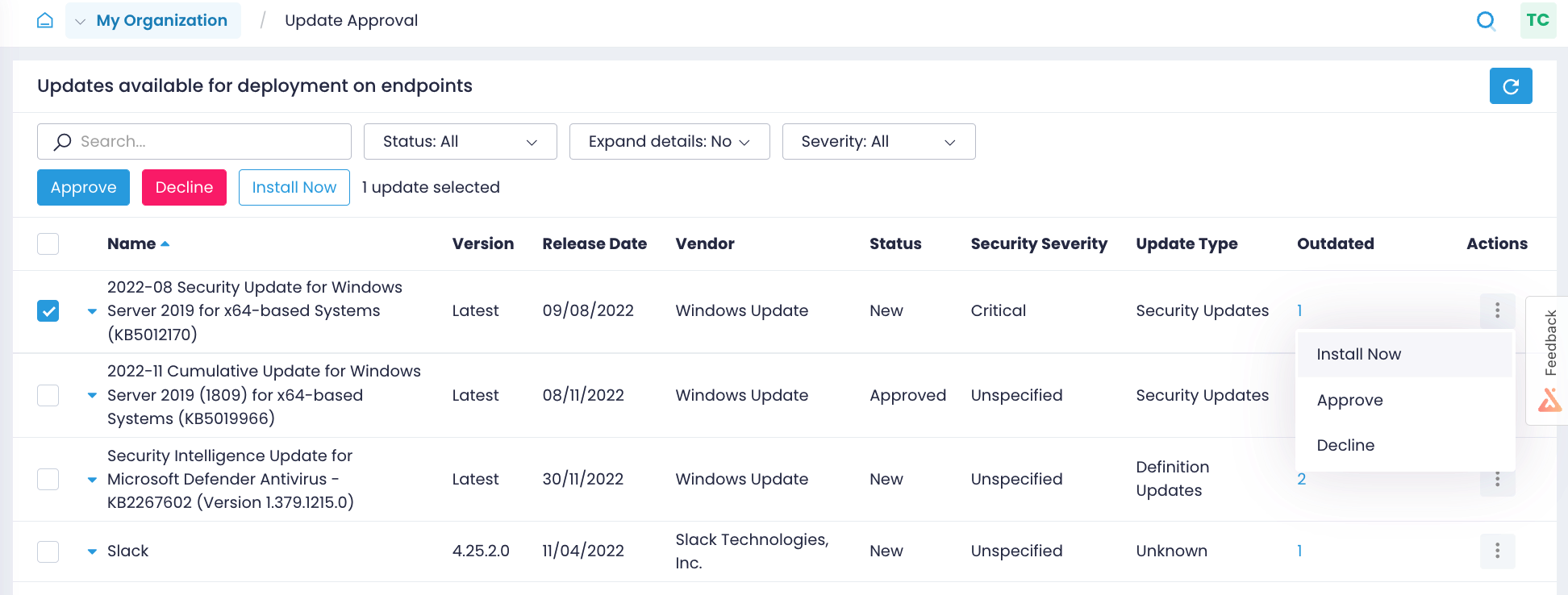
Automate patch management
Keep your OS and third-party applications, including your custom and proprietary software, up to date with the latest patches. Update all servers and workstations consistently, even if they are remote, not connected to a corporate VPN, not joined to a domain, or offline.
Identify available patches
Never miss a critical or security patch. Find out what updates are available for Windows OS and third-party applications but missing from your endpoints, and get notified of new Windows updates.
Enforce flexible policies
Prioritize patches by severity, test them on isolated systems, approve updates for deployment, and schedule patch implementation within defined patch windows to minimize downtime.
Demonstrate compliance
Verify in real time that patches have been successfully applied. Prove to auditors that you have a working patch management procedure with detailed reports on installed patches and patching history.
II.C.10(a); II.C.10(b); II.C.10(c); II.C.12; II.C.13(a); II.C.15(d); IV.A
Enforce secure endpoint configurations
Harden your endpoint environment with security configurations applied consistently across any group of endpoints, whether onsite or remote, enterprise- or employee-owned, or new or existing ones.
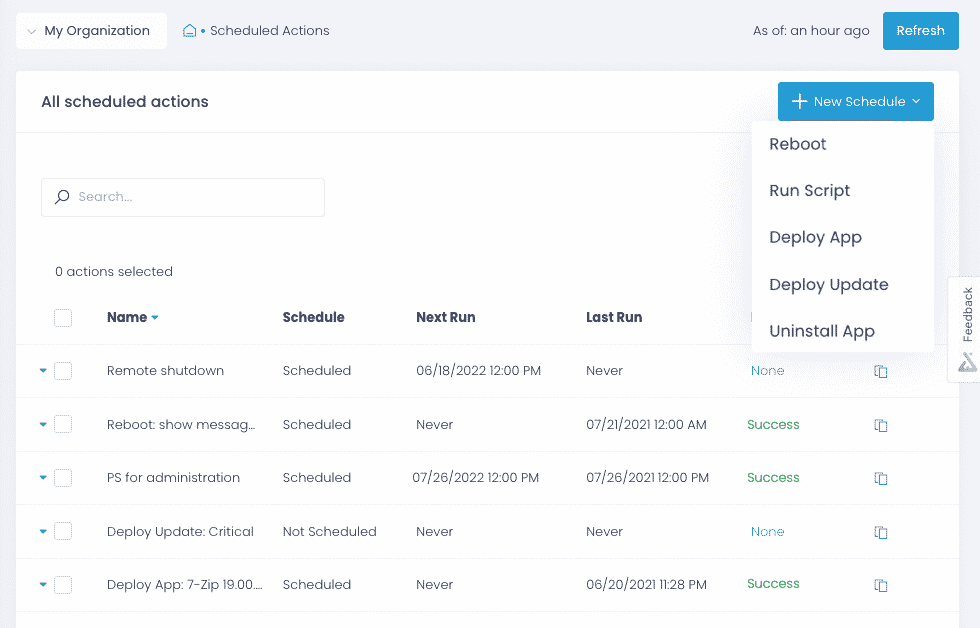
Automate policy enforcement
Enforce security configurations, such as enabling encryption and logging, removing local admin rights, and wiping data remotely, individually or en masse with ready-to-use and custom scripts.
Create standard builds
Build your own configuration standards with multi-step policies and apply them automatically to different groups of endpoints, including devices newly introduced to your environment.
Detect misconfigurations
Detect unauthorized configuration changes with real-time alerts. Use reports to ascertain that required security controls are working and identify misconfigurations that need to be fixed.
II.C.5; II.C.10(b); II.C.11; II.C.12; II.C.13(a); II.C.15(d); IV.A
Keep up-to-date asset inventory
Automate asset inventory and gain accurate, real-time insights into the software and hardware used, no matter where your endpoints are located. Know what devices you have, how they are configured, what software is being used, and which devices need upgrades.
Maintain hardware inventory
Get an overview of endpoint hardware to make informed decisions about necessary replacements and upgrades, and ensure it is up-to-date, vendor-supported, and compliant.
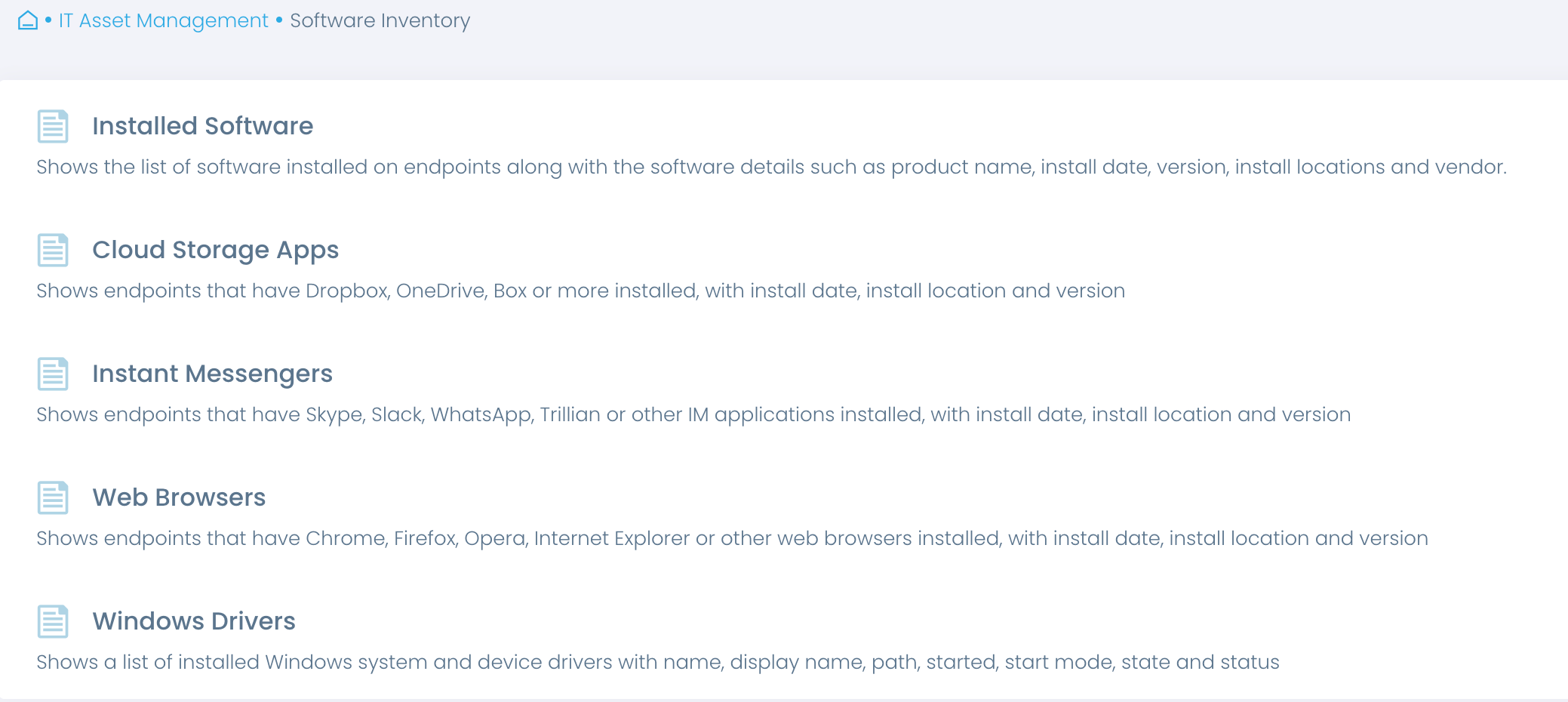
Automate software inventory
Learn what software is in use, with insights into versions, installation dates and more. Get a complete overview of all installed software or focus on specific types, such as cloud storage and instant messengers.
Detect unauthorized software
Streamline periodic reviews to verify that only authorized, up-to-date, and supported software is in use. Detect unauthorized, obsolete, or unsupported software that needs to be disposed of.
II.C.10(b); II.C.10(c); II.C.11; II.C.12; II.C.15(c); II.C.15(d); IV.A
Manage software assets
Deploy security solutions and allowed business applications, detect unauthorized installations, uninstall unauthorized software, and replace obsolete software efficiently and at scale. Your endpoints don’t need to be connected to a corporate network or VPN, or joined to a domain.
Deploy authorized software
Deploy approved software, including firewalls, anti-malware, DLP and other security solutions, automatically from a single location. Choose from ready-to-deploy apps, or upload your custom software.
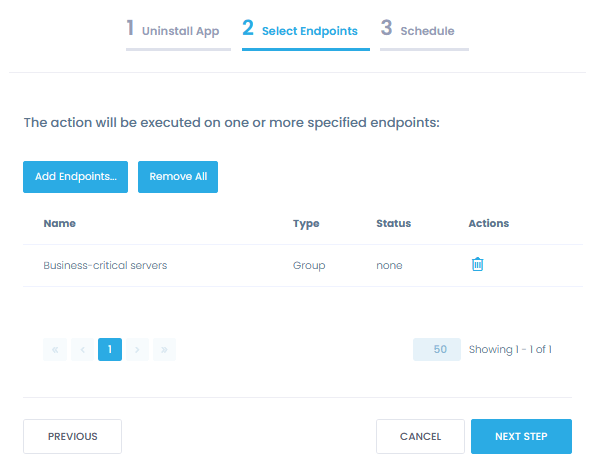
Remove unauthorized software
Uninstall unauthorized applications from multiple endpoints at once, forcing a reboot if necessary to complete the process. Replace unsupported software in one go with multi-step policies.
Detect software changes
Be notified in real-time about changes that can bring you out of compliance, such as unauthorized software installations or the removal of an anti-malware solution, to respond promptly.
Secure and Compliant Solution
At Action1, security is our top priority. Action1 not only helps organizations meet FFIEC guidelines, but is also a secure solution itself, compliant with application security, remote access, and other FFIEC recommendations.
Security features
Action1 enforces two-factor authentication, provides role-based-access and audit logs, and secures all connections with TLS 1.2 and AES-256.
Compliant solution
Action1 meets the requirements of security standards and regulations, such as SOC 2, ISO/IEC 27001 and NIST SP 800-171.
Secure remote access
Action1 saves you from additional holes in your firewall configuration, such as opening an inbound port for remote connections to resources.
Trusted by thousands of IT teams around the world
10M+
Managed Endpoints
3,000+
Customers
99%
Patch success rate


Why customers choose Action1
Tame complexity
Get up and running and start getting value in an hour with a solution that is easy to deploy and just works. No legacy technology, clunky tools, and features you don’t need.
Get it done in one place
Patch business-critical systems and applications, deploy and remove software, inventory assets, configure and monitor endpoints—all from a single platform.
See phenomenal ROI
What Our Customers Say
Action1 slashed times to bring our environment in line with our IT security policies from 6 hours a week to just 20 minutes a week, which is 18 times faster than with our previous approach.
Thanks to Action1, I am able to check off a couple of boxes on a GLBA compliance list. First, it helps us remediate security vulnerabilities in a timely manner while saving us 15 hours per week on patch management. Second, it includes reporting functionality, which the Safeguards Rule also requires.
One of the elements that we especially appreciate in Action1 is the power of scripting. By using advanced PowerShell scripts through the platform, we were able to fully automate our workstation build process — making it 9 times faster whilst increasing quality.
Frequently asked questions
Why is patch management important for the financial industry?
Patch management is critical for the financial industry due to the high value of the data it protects and the strict regulatory requirements it must adhere to. Financial institutions handle sensitive information such as customer banking details, personal identification, and financial transactions, making them prime targets for cyberattacks. Any vulnerabilities in their software or systems can lead to severe consequences, including data breaches, financial loss, and reputational damage. Additionally, regulatory bodies such as PCI DSS and GDPR require financial institutions to maintain high levels of security and regularly update their systems to address known vulnerabilities. By ensuring that all software is regularly patched, financial institutions reduce the risk of cyberattacks, improve the stability of their systems, and remain compliant with industry regulations. Patch management also ensures that operational processes, such as online banking, stock trading, and payment systems, run smoothly without disruptions.
What are the most common vulnerabilities in the financial sector?
The financial sector faces a range of vulnerabilities due to its complexity and the value of the assets it manages. Common vulnerabilities include outdated software and operating systems that have not been patched for known security flaws, making them an easy target for cybercriminals. Financial institutions are also susceptible to phishing attacks, which can lead to unauthorized access to systems and sensitive data. Additionally, third-party applications and services often integrated into financial systems may have weak security measures, creating potential entry points for attackers. Another common vulnerability is misconfigured networks or weak access controls, which can expose internal systems to unauthorized users. With the growing reliance on digital services, maintaining secure cloud environments and protecting against insider threats also remain key challenges for the financial industry.
How does Action1 help with financial industry patch management?
Action1 assists the financial industry in patch management by offering a cloud-based, automated solution that ensures critical systems remain secure and up-to-date. With Action1, financial institutions can easily monitor and deploy patches across multiple devices and locations, reducing the risk of vulnerabilities being exploited. The platform provides centralized control and visibility into the patching process, which is essential for maintaining compliance with regulatory standards and preventing costly security breaches. By automating the patching process, Action1 minimizes the manual work required from IT teams, allowing them to focus on other mission-critical tasks. Furthermore, Action1’s real-time reporting and audit capabilities ensure that financial institutions can demonstrate compliance with industry regulations, while also providing a quick response to emerging threats or vulnerabilities.