Vulnerability Assessment
Action1 automatically performs real-time vulnerability assessment for operating systems and software installed on your managed endpoints and helps you remediate vulnerabilities in accordance with your company policies.
The initial vulnerability assessment is free for an unlimited number of endpoints – all you have to do is deploy Action1 agents to your endpoints using one of the provided deployment methods. Once the agents are deployed, they detect all software vulnerabilities and send this data to Action1 cloud. The ongoing vulnerability assessment and remediation capabilities are always free and never expire for your first 200 endpoints. A paid subscription can be purchased to cover any additional endpoints for ongoing assessment (beyond the free initial assessment) and remediation.
Tip: Make sure your endpoints are connected to Action1 Cloud. Check out the Endpoints view to see your managed endpoints and their connection status.
Vulnerabilities on Dashboard
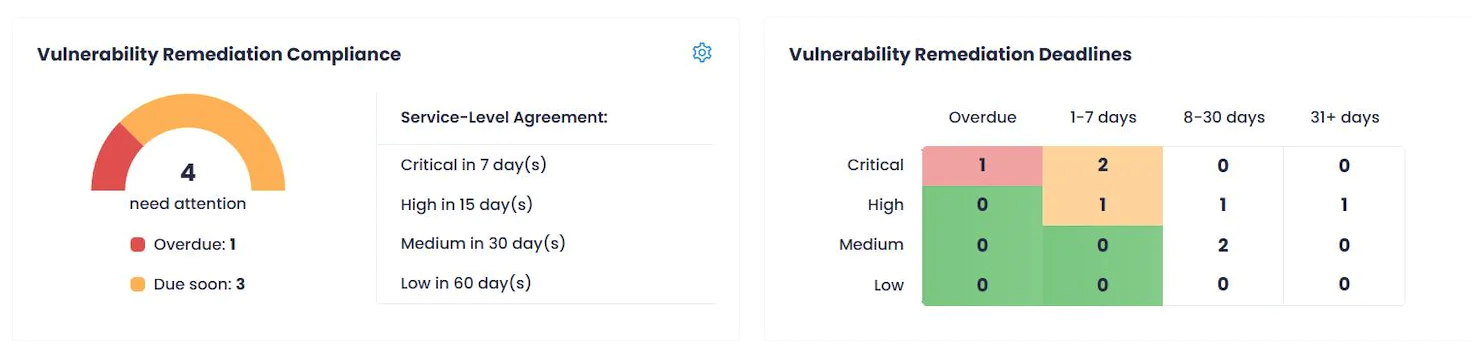
Navigate to the Dashboard to get a bird’s eye view of your organization’s security posture. Check Vulnerability Remediation Compliance and Vulnerability Remediation Deadlines dashboard widgets to get an overview of your compliance status, see the number of CVEs that need your attention and the remediation timeframe which is defined by your corporate service-level agreements. See Configure SLAs.
For tips on how to leverage these dashboards, see Dashboard.
Vulnerabilities View
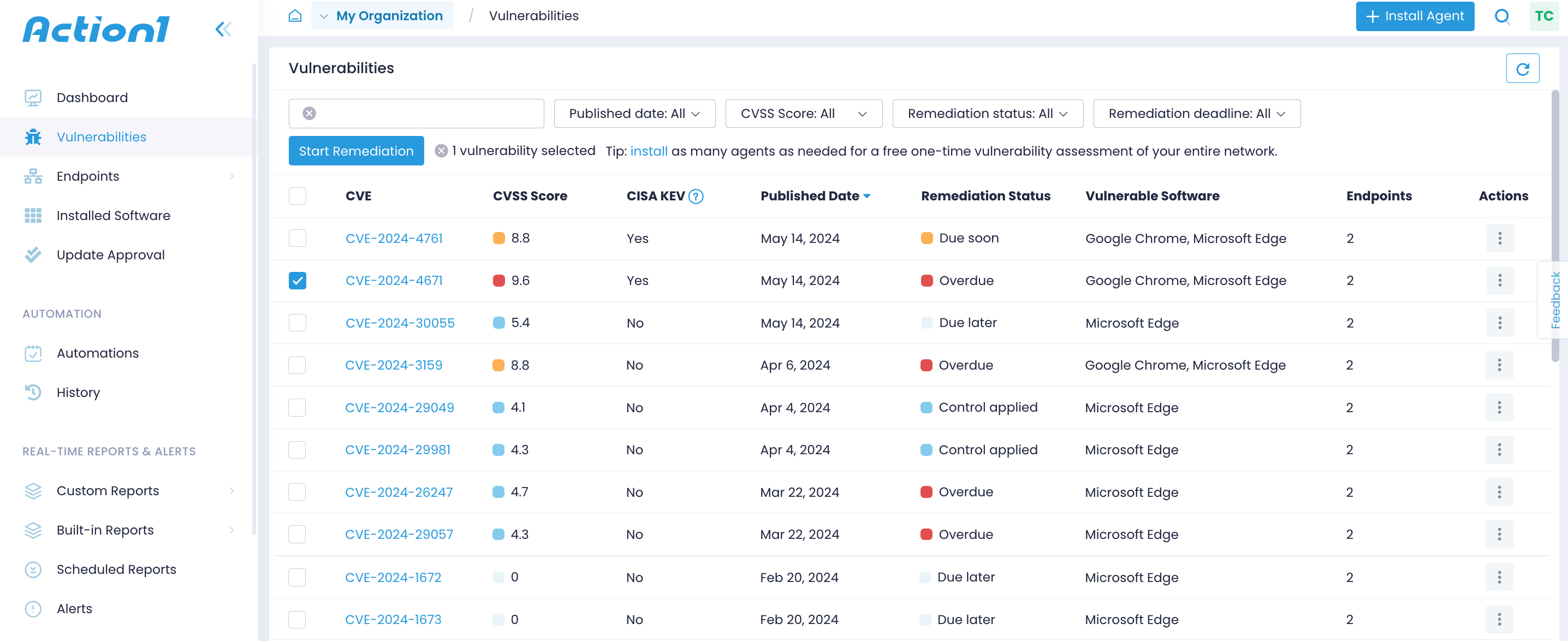
Navigate to the Vulnerabilities view to see all detected common vulnerabilities and exposures (CVEs). Action1 detects all software vulnerabilities in real-time, such as OS, browsers, Microsoft 365, administration tools, and more.
Action1 provides a complete reference for each vulnerability such as its identifier, CVSS score, attack vector, the date it was published, whether it is known to be actively exploited (listed in CISA KEV) or used in any ransomware campaigns, and more. The CVE identifier includes the year the issue was found and its number in the NIST National Vulnerability Database, e.g., CVE-2023-4073. The CVSS score, which can be between 0 and 10 is determined based on a variety of factors such as attack complexity, exploitability, and impact on your infrastructure.
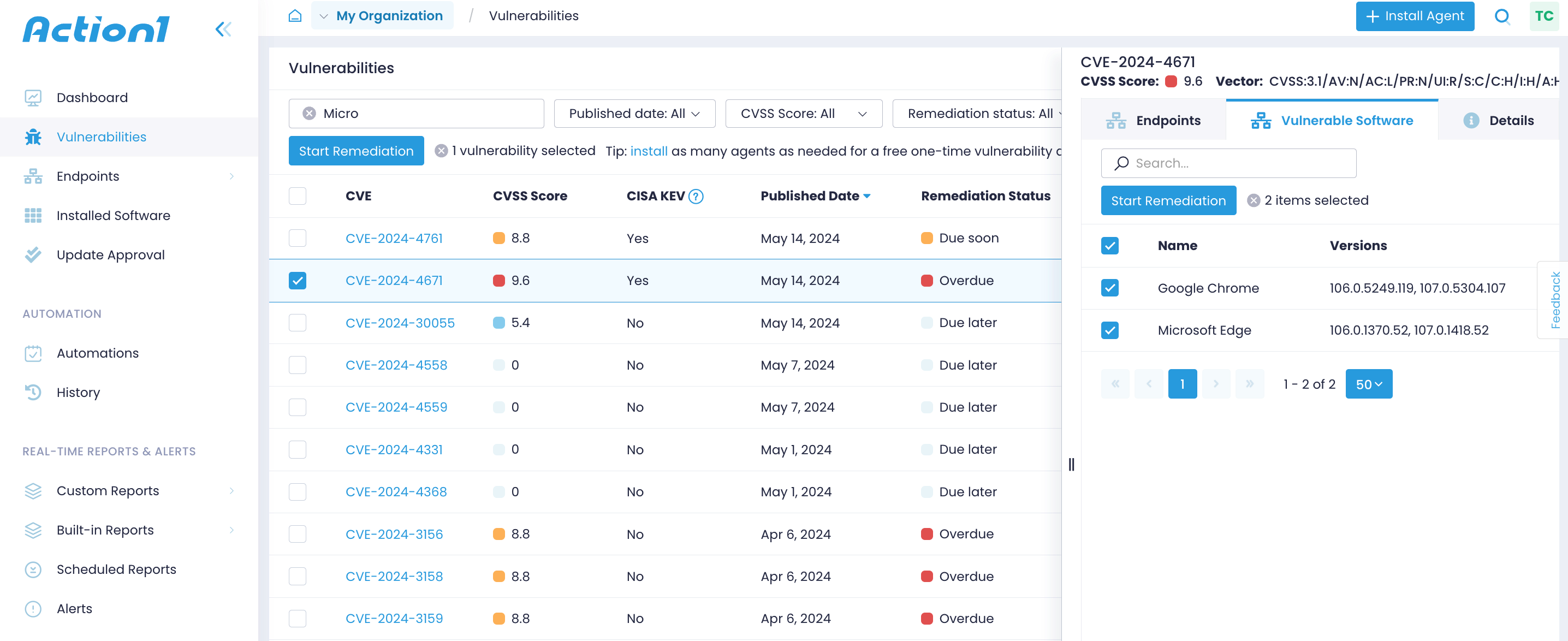
Expand the vulnerability details to see the affected endpoints, compromised software or OS, and other details, including the attack vector, attack complexity, and a link to the NIST National Vulnerability Database.