CIS Compliance Software
For Securing Onsite and Remote Endpoints
Automate Windows OS and application patching
Inventory software assets and endpoint hardware
Enforce secure endpoint configurations
Deploy security software to servers and workstations
Achieve and Maintain CIS Compliance with Action1
The Center for Internet Security (CIS) framework is a set of best practices for securing an organization’s IT systems and data. It provides a list of security controls organizations can implement to improve their cybersecurity posture and protect themselves from cyber threats and data breaches. CIS compliance software from Action1 helps you adhere to the following specific CIS critical security controls:
CIS Control 1: Inventory and Control of Enterprise Assets
CIS Safeguard 1.1
CIS Control 2: Inventory and Control of Software Assets
CIS Safeguards 2.1; 2.2; 2.3; 2.4
CIS Control 3: Data Protection
CIS Safeguard 3.6
CIS Control 4: Secure Configuration of Enterprise Assets and Software
CIS Safeguards 4.3; 4.4; 4.5; 4.7; 4.10; 4.11
CIS Control 7: Continuous Vulnerability Management
CIS Safeguards 7.2; 7.3
CIS Control 9: Email and Web Browser Protections
CIS Safeguards 9.1; 9.4
CIS Control 10: Malware Defenses
CIS Safeguards 10.1; 10.3
CIS Control 13: Network Monitoring and Defense
CIS Safeguards 13.2; 13.5; 13.7
CIS Controls 1.1; 2.1; 2.2; 2.3; 2.4; 9.1; 9.4:
Establish and maintain asset inventory, ensure the use of authorized software and address unauthorized software
Maintain up-to-date inventory
Automate asset inventory for all your Windows workstations and servers and gain accurate real-time insights into software and hardware. Know what devices you have, how they are configured, what software is being used and what devices need an upgrade.
Maintain detailed endpoint hardware inventory
Get an overview of endpoint hardware to make informed decisions about required hardware replacements and upgrades and ensure hardware remains current, supported by the vendors and compliant.
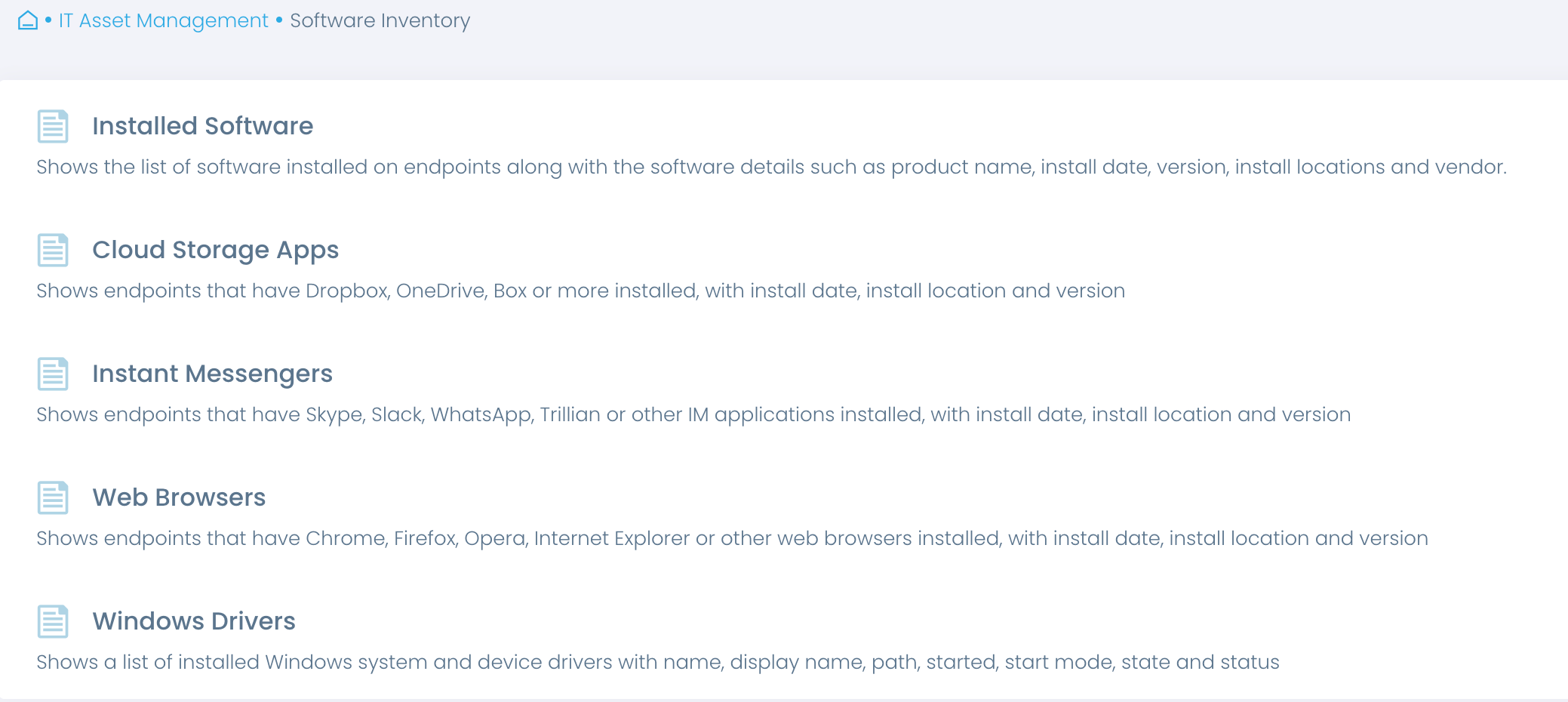
Automate software inventory
Know exactly what software is installed on endpoints, with insights into versions, installation dates and more. Get a full overview or focus on specific types, such as cloud storage and instant messengers.
Address unauthorized software
Verify that only authorized applications are in use, including browsers, email clients and their extensions. Detect unauthorized applications and extensions and automate their removal.
CIS Controls 7.2; 7.3:
Perform automated operating system and application patch management
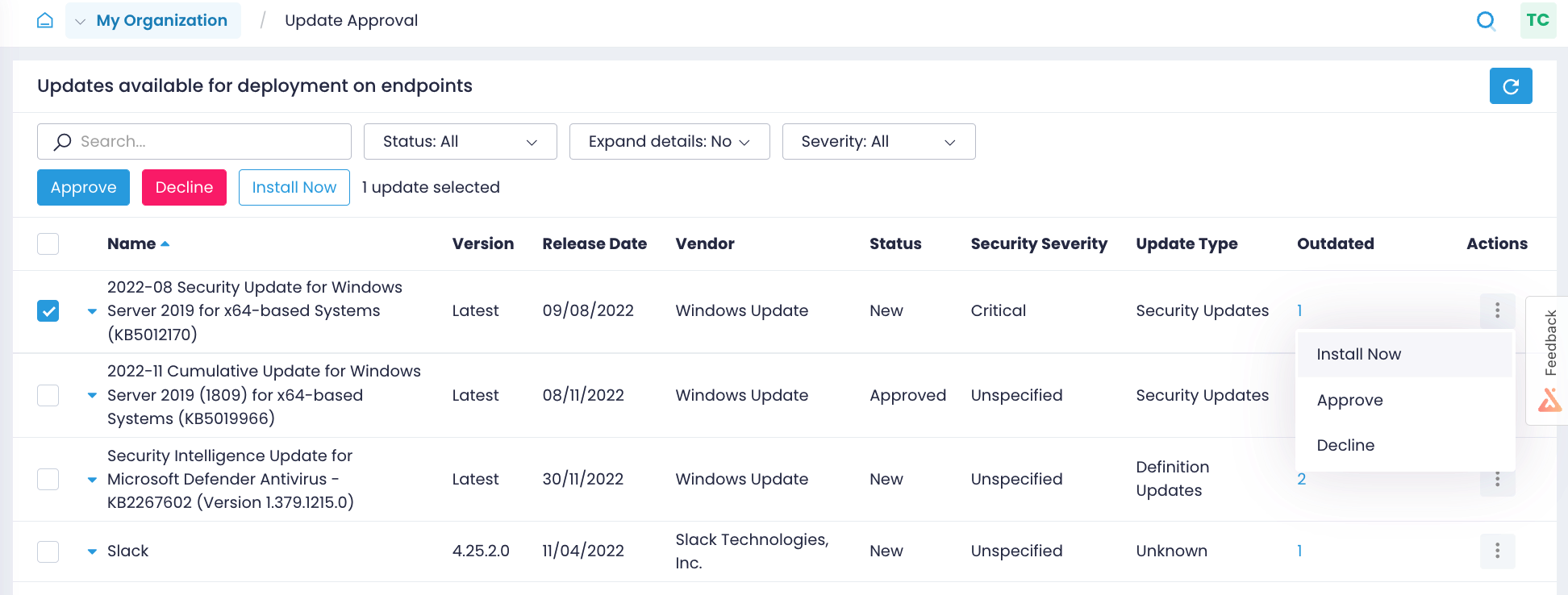
Automate patch management
Implement a reliable and consistent patch management process, regardless of where your endpoints are. Automate the entire process, from identifying missing patches, to installing updates to multiple endpoints in minutes and verifying patching results.
Update operating systems
Keep Windows OS consistently patched on all your workstations and servers, even if they are not on a corporate network, disconnected from a company VPN, not joined to a domain, or offline.
Patch third-party applications
Automatically update most common applications, curated by Action1. Upload new versions of your custom and proprietary applications and update them from the same console.
Identify missing updates
Close the window of opportunity for attackers by identifying what Windows OS and third-party application updates are missing on what endpoints and getting alerts on new Windows updates.
CIS Controls 3.6; 4.3; 4.7; 4.10; 4.11; 10.3:
Establish and maintain the secure configuration of end-user devices, servers and software; encrypt data on end-user devices and disable autorun for removable media
Enforce secure endpoint configurations
Build and maintain secure configurations that adhere to both the high-level CIS control framework and more specific CIS Benchmarks.
Automate the enforcement and validation of virtually any configuration across any number of endpoints, whether onsite or remote, enterprise- or employee-owned, or new or existing ones.
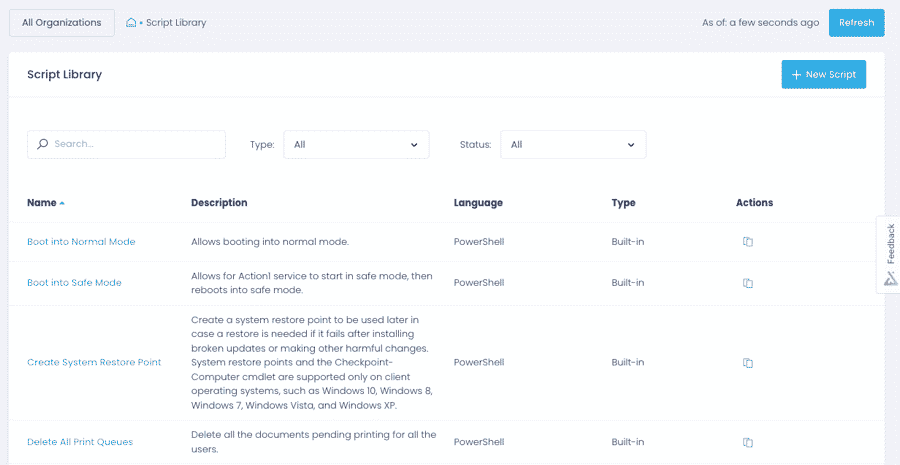
Automate policy enforcement
Apply security configurations, such as enabling BitLocker, disabling default accounts, enforcing session timeout and wiping data remotely, across onsite and remote endpoints with built-in and custom scripts.
Verify security controls
Ascertain that your endpoint security controls are running with pre-built and custom reports, and get real-time alerts when someone tampers with endpoint configurations, accidentally or intentionally.
Onboard new devices
Prevent insecure configurations from being introduced into the environment with a new device by applying CIS controls and benchmark recommendations to new devices automatically with multi-step policies.
CIS Controls 4.4; 4.5; 10.1; 13.2; 13.7:
Deploy and maintain a firewall, anti-malware software, and host-based intrusion prevention and detection solutions on servers and end-user devices
Deploy and update security solutions
Ensure that your servers and end-user workstations are continuously protected with authorized and up-to-date security solutions, such as firewalls, anti-malware and intrusion detection and prevention systems.
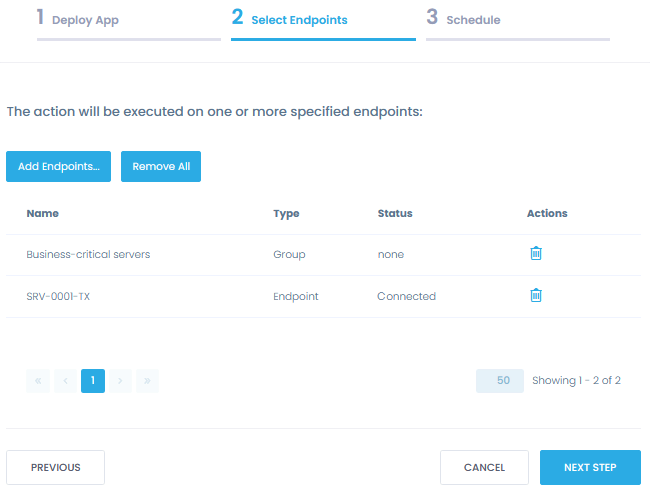
Deploy security software
Automate the deployment of firewalls, anti-malware and other security solutions across any number of endpoints from a single App Store. Choose from ready-to-deploy applications, or upload your custom software.
Update security solutions
Update security software timely and consistently from a single location. Automatically patch applications, tested by Action1, or upload new versions of your custom applications for further testing and deployment.
Detect changes to security software
Get real-time alerts on changes to your security software that can make your endpoints vulnerable to attacks bring you out of compliance, such as removing an anti-malware solution from any endpoint.
Secure and Compliant CIS Compliance Tool
At Action1, security is our top priority. Action1 not only helps organizations implement CIS controls, but is also a secure solution itself, applying CIS recommendations and best practices to protect our users.
Security features
Action1 enforces two-factor authentication, provides role-based-access and audit logs, and secures all connections with TLS 1.2 and AES-256.
Compliant solution
Action1 is compliant with the requirements of security standards and regulations, such as SOC 2, ISO/IEC 27001 and NIST SP 800-171.
Secure remote access
Action1 saves you from poking extra holes in your firewall configuration, such as opening an inbound port for remote access to endpoints.
Trusted by many Fortune 500 companies
10M+
Managed Endpoints
3,000+
Customers
99%
Patch success rate


Why customers choose Action1
Tame complexity
Get up and running and start getting value in one hour with a solution that is easy to deploy and just works. No legacy technology, clunky tools, and feature overload.
Do it all in one place
Patch operating systems and applications, deploy security software, configure endpoints and maintain asset inventory — all from a single centralized location.
Stay flexible
Enable patch management, inventory and secure endpoint configuration the way your organization needs, with granular, easily customizable policies.
Break free from VPN
Update and manage remote and onsite endpoints with Action1 cloud-native platform. No company network, domain, VPN or driving is required.
Reach offline devices
Automatically catch up on updates, software deployment and script execution tasks as soon as offline endpoints get back online.
See phenomenal ROI
What Our Customers Say
Without adequate patch management in place, I would have to go around to each individual machine to keep them updated. It could leave us open to security vulnerabilities, as a manual approach always leaves a gap for patches to be missed