Anonymous security researcher demonstrates hijacking of Packagist packages


Anonymous security researcher demonstrates hijacking of Packagist packages

In this issue: May 2023 Patch Tuesday updates, fixes for Google Chrome, Firefox, Apache, Service Location Protocol, VMware, Android, Apple, Intel, and Linux.

In a recent interview at Piper Sandler’s Cybersecurity CEO Summit in San Francisco, Kevin Mandia highlights the importance of patching as a primary solution to mitigate cyberattacks, citing exploitation as a major reason for their success.

Timely patching of applications and systems is a critical requirement for smart cities along with MFA, zero trust, and other cybersecurity best practices.

In the past few days, our users have asked us numerous questions regarding the potential hack of the Action1 platform. This concern has arisen due to a recent article in Bleeping Computer. We would like to reassure our users that Action1 has not been compromised, and their accounts remain safe from potential threats.

A recent US Government Accountability Office (GAO) audit report reveals a significant number of outdated software systems and technologies within the Internal Revenue Service (IRS).

April 2023 Patch Tuesday updates, fixes for Microsoft Snipping Tool, Google Chrome, Firefox, Android, Bing, IEEE 802.11 Wi-Fi protocol, and Apple.
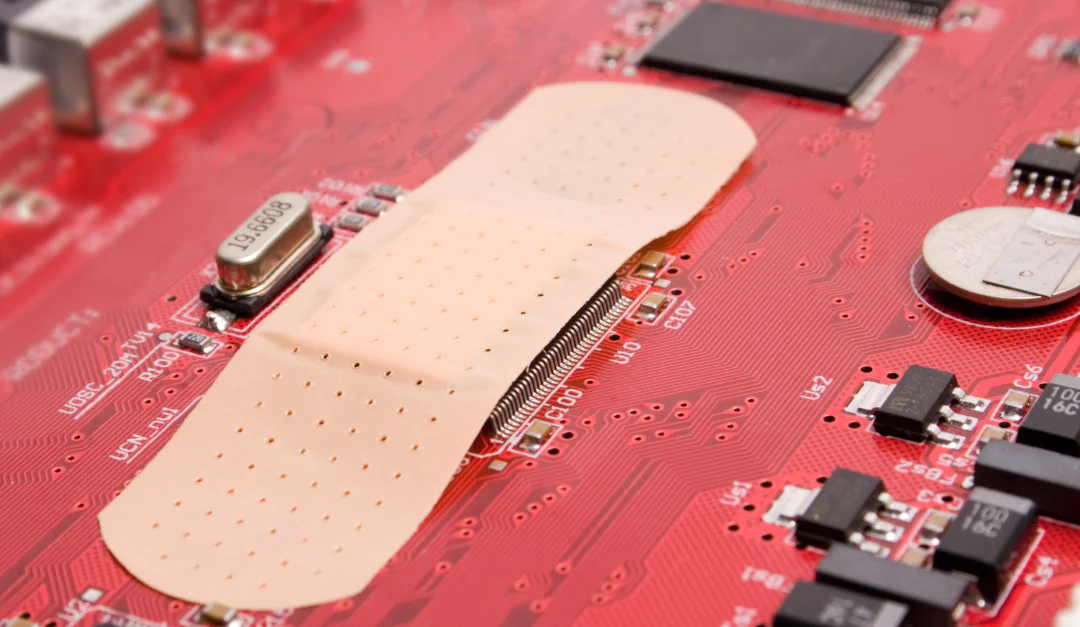
Make patching of actively exploited vulnerabilities in Internet-exposed devices your #1 priority to reduce your chances of being breached by 99%.

Action1, a leading risk-based patch management platform for distributed networks, is proud to announce that it has received an impressive 63 badges in the 2023 Spring G2 reports in various categories, including Patch Management, RMM, Endpoint Management, Remote Desktop, and Remote Support.

3CX has fallen victim to a supply chain attack affecting multiple versions of its desktop app. Action1 helps mitigate the risks with a script terminating all running 3CXDesktop processes and prevents their auto-launch at the next system reboot.

Discover if your Azure AD instance has any misconfigured applications allowing unauthorized access to external users

Highlights of some recently exploited vulnerabilities that need to be patched or remediated ASAP.

Microsoft’s Bret Arsenault says patch management is a part of his day-to-day burden despite evolving AI capabilities

Microsoft has identified and patched a zero-day vulnerability in its popular email client Outlook. However, if you use a Click-To-Run version of Microsoft Office, you may not receive this update via Microsoft Update.

Experts say that only a small percentage of vulnerabilities present the biggest risk, here are some of most the important vulnerabilities that need to be patched as they are being actively exploited.

Rogue NuGet packages infect developer machines with malware raise concerns over public open source repository security in general.

America’s cyber defense agency issues the updated cybersecurity performance goals (CPG) highlighting risk-based vulnerability assessment and patch management as core goals.

LockBit ransomware group executed a ransomware attack on SpaceX’s contractor. One of the methods generally used by this group is exploitation of unpatched vulnerabilities.

Threat actors successful in remote code execution due to CVSS score 9.8 vuln that had a patch for over 3 years; CISA recommends implementing a patch management solution as mitigation.

TSA recently announced new requirements for the air travel industry that includes patching of systems as a major component.