Table of Contents
What is vulnerability remediation?
The difference between remediation and mitigation
Step 1. Assess IT infrastructure
Step 2. Identify Vulnerabilities
Step 3. Prioritize
Step 4. Fix the issues
Step 5. Follow up
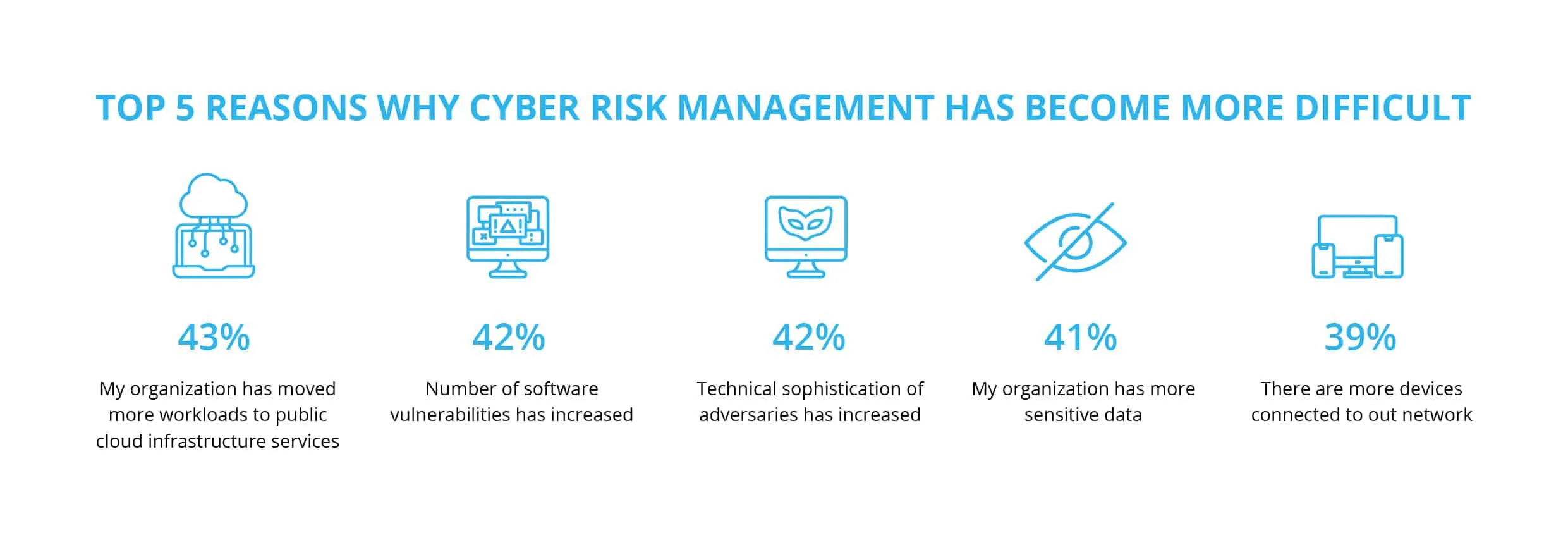
Vulnerability remediation is a crucial facet of digital risk management when dealing with vulnerable software applications. This article explains the importance of vulnerability remediation and the steps involved in the process.
What Is Vulnerability Remediation?
Vulnerability remediation means neutralizing security loopholes before they become threats. This is typically done through patching software applications. In some cases, remediation may also involve hardware fixes, upgrades, or replacements.
A vulnerability remediation plan is vital for preventing devastating data breaches and other forms of cyberattacks. It’s also a partial requirement for various data security compliance standards.
Remediation vs. Mitigation
Although security vulnerability remediation and mitigation may sound the same, they are two very different approaches to dealing with security flaws. While remediation aims to eliminate the vulnerability, mitigation is more of a workaround to minimize the likelihood of a vulnerability being exploited.
Mitigation is usually not the final answer to solving a security problem. It’s only used where remediation measures are not possible or feasible. For instance, if a patch is unavailable, the security team might offload the flawed software to buy time until a permanent fix is developed. Also, remediation might experience pushback from the organization, mostly to avoid downtime, forcing the security team to mitigate a vulnerability instead.
The Vulnerability Remediation Process
Vulnerability remediation management is a continuous multi-stage process. Below are the five vulnerability remediation steps to successfully managing software-based security risks.
1. Assess your IT infrastructure
Before you can start fixing and patching, you need to know where to find vulnerabilities. A comprehensive IT audit gives you a detailed overview of the entire digital estate. It shows you all the software and hardware resources in active use, along with important security information such as each component’s build version, update logs, and third-party dependencies.
2. Identify vulnerabilities
After auditing your IT, the next step is running a vulnerability assessment remediation. Check for any possible flaws lurking in all corporate software tools, from operating systems and ERPs to basic file readers. It’s not practical or even possible to do this manually. So, it’s best to use automated tools to scan your entire system for missing updates, patches, and fixes. These tools can quickly compare vendor release notes to the software’s update logs to determine its security status.
3. Make a priority list
Create a priority list for which of the newly discovered vulnerabilities to remediate first. Prioritize the vulnerability with the highest severity scores and those more likely to be exploited. However, prioritizing is not always this straightforward. Many security experts consider vulnerability prioritization their top remediation challenge.

- The type and popularity of the application
- Ease of remediation
- The remediation’s impact on the IT ecosystem
- The vulnerability’s disclosure date and urgency
4. Apply fixes
After deciding which vulnerabilities to fix, it’s only a matter of applying the necessary patches to the corresponding applications. Although some business systems may have to shut down during this step, plan out the patch deployment process to avoid unnecessary downtime. And remember, it’s not just about being fast; you also need to be thorough and precise.
5. The follow-up
The final step is to assess whether all vulnerabilities were fixed correctly and the remediation’s impact on the applications and their dependencies. Ideally, you should test each newly patched application to ascertain the remediation’s effectiveness. You need to follow up on patched systems because remediation can sometimes yield unexpected and undesirable results.
Vulnerability remediation is a long and cyclic process. But it’s so much easier when using automated tools. Discover a smarter, quicker, and effortless way to secure your digital assets with Action1 solution for creating patch management policies. Sign up for a free trial today and get a taste of this much-needed security reassurance.




