In the rapidly evolving landscape of cybersecurity, staying ahead of vulnerabilities is vital. That’s why we’re thrilled to present to you the powerful vulnerability remediation features of Action1’s latest release. The updated Action1 platform brings together vulnerability discovery and remediation, helping you fortify defenses against threats such as ransomware infections and security breaches.
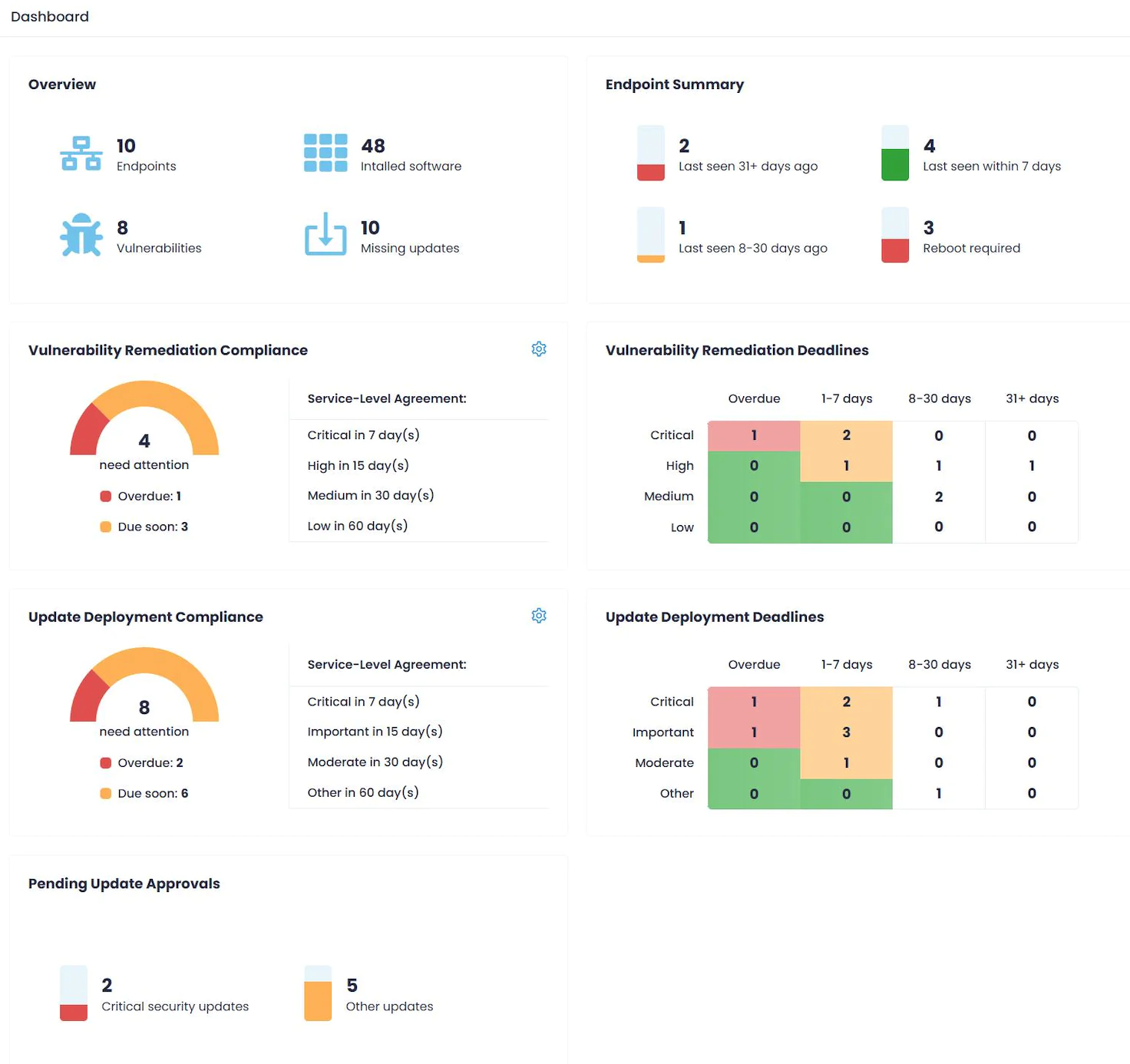
The real-time detection of vulnerabilities across the enterprise fleet of endpoints is based on data about 200,000+ vulnerabilities from multiple external threat intelligence sources, provides instant visibility into them for better prioritization decisions, and allows automated remediation of these vulnerabilities.
Are you ready to explore why we’re genuinely excited about these game-changing capabilities? Let’s dive right in!
1. Effortless Vulnerability Detection and Resolution
Action1 simplifies the process of identifying vulnerabilities in third-party software across your managed endpoints. The Vulnerabilities dashboard becomes your central hub, offering a comprehensive view of all identified common vulnerabilities and exposures (CVEs) within your network. It’s a game-changer when it comes to addressing vulnerabilities effectively.
2. A Wealth of Vulnerability Insights
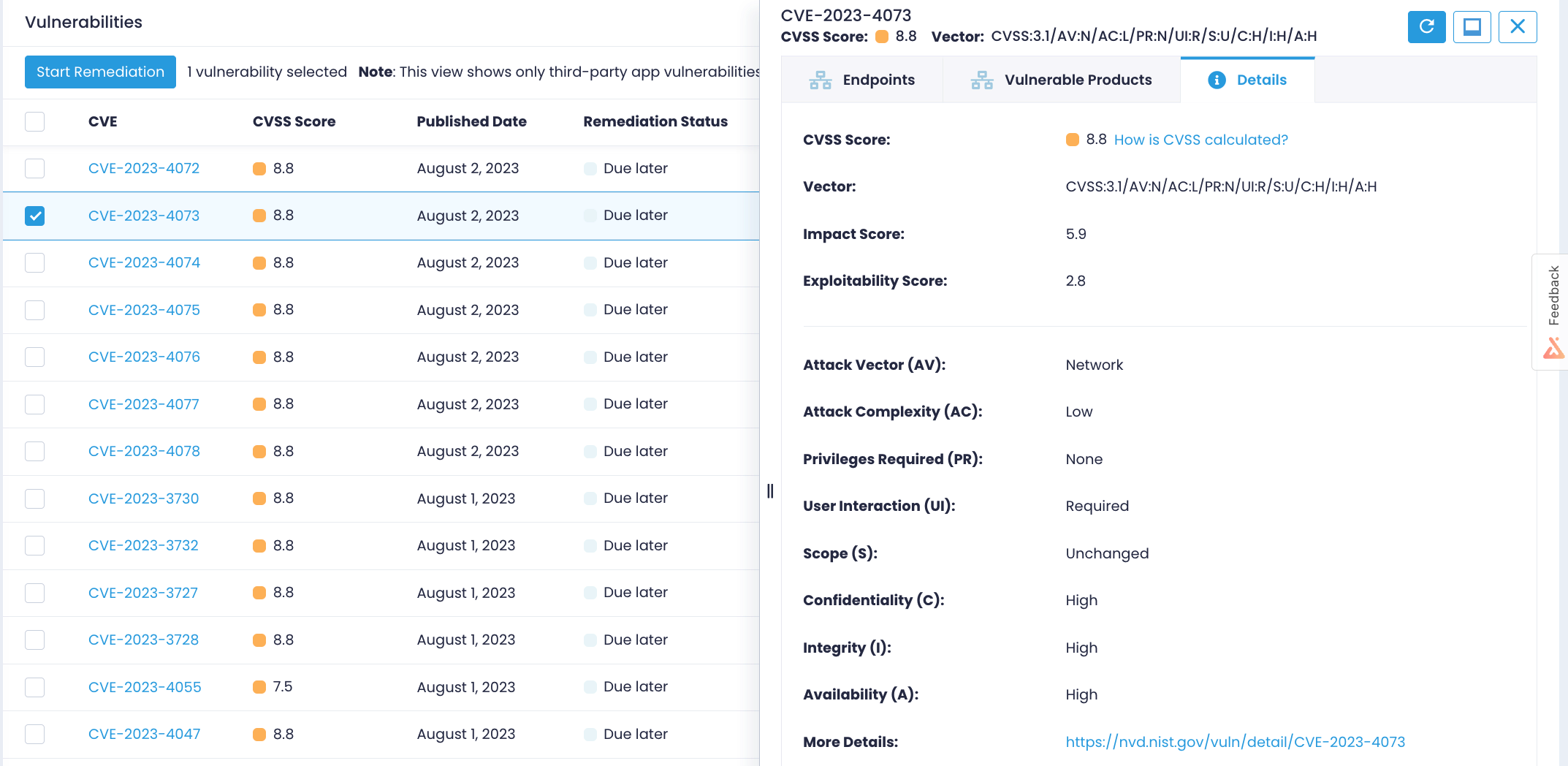
Equipped with a repository of detailed vulnerability information, Action1 empowers you with critical data. From identifiers to CVSS scores, publication dates to impacted products – all pertinent details are presented for your convenience. Dive deeper into vulnerability specifics, including vectors, attack complexities, and direct links to the NIST National Vulnerability Database. Informed decision-making has never been so straightforward.
3. Customizable Remediation Timeframes
The flexibility of Action1’s vulnerability remediation features shines through in its adaptable timeframes. By combining industry best practices and service-level agreements (SLAs), Action1 calculates deadlines based on vulnerability severity. Critical vulnerabilities demand immediate attention, while lower-impact vulnerabilities come with more relaxed timelines, aligning perfectly with your corporate patching policy.
For example,
- critical vulnerabilities (9-10) must be addressed in a day,
- high impact vulnerabilities (7-9) must be mitigated within 15 days,
- medium vulnerabilities (4-7) must be treated in 1 month,
- low impact vulnerabilities (1-4) must be mitigated within 2 months.
You can adjust SLAs based on your corporate patching policy. For example, to ensure critical issues get addressed as soon as possible, you can make them prominent by keeping their deadlines tight while loosening those for low- and medium-risk CVEs.
4. Simplified Vulnerability Management
Witness the power of Action1 as it streamlines vulnerability management across multiple endpoints simultaneously. With an array of remediation strategies at your disposal, from installing updates to uninstalling applications or implementing compensating controls, addressing security threats becomes a seamless process.
5. Intelligent Policies for Automated Execution
Discover the intelligence behind Action1’s smart policy creation. After setting up a remediation policy, Action1 takes charge, ensuring policies are executed meticulously according to your schedule. Easily locate policies awaiting execution through the Policies section, and gain insights into past vulnerability management actions via the Policy History.
Leverage Action1’s Vulnerability Remediation
The features of Action1’s vulnerability remediation capabilities emphasize a commitment to enhancing your cybersecurity posture. In a landscape where vulnerability exploitation ranks among the top three attack methods, the updated Action1 platform plays a crucial role in reducing the mean-time-to-remediate (MTTR) vulnerabilities, thus assisting organizations in mitigating this risk significantly.




