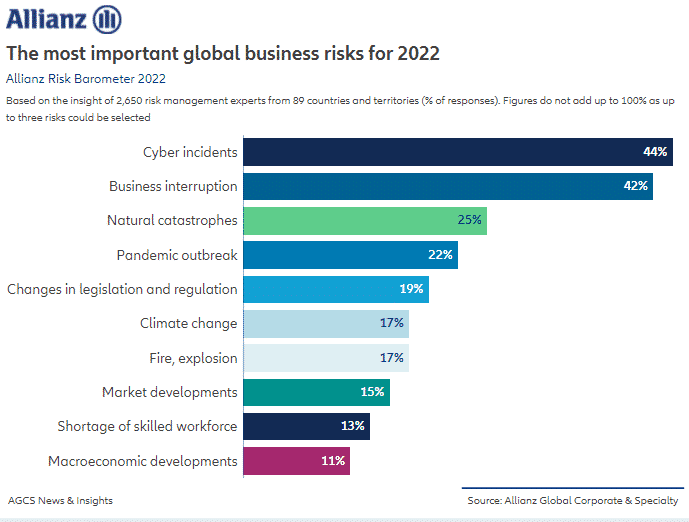
As the business world grows ever more reliant on data and technology, the risk profile for many organizations continues to expand. Cybersecurity is by far the most disconcerting and widespread concern of the many different types of security risks to organizations. The Allianz Risk Barometer ranks cyber incidents (cyberattacks, IT outages, data breaches, etc.) as the number one business risk in 2022. For perspective, cyber threats are up there with business interruptions, natural catastrophes, pandemic outbreaks, and climate change.
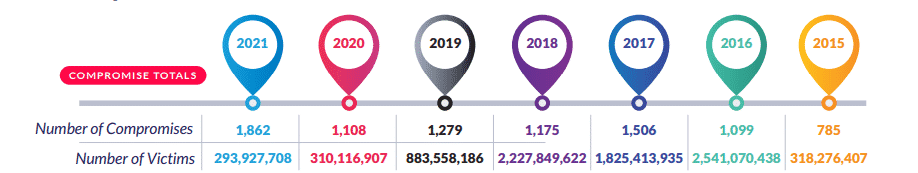
Business leaders, entrepreneurs, and security experts have many valid reasons to dread cyberattacks. One, cyberattacks are becoming more common, indiscriminately victimizing all organizations, including SMBs, non-profits, and learning institutions. Two, cybercriminals are deploying increasingly more sophisticated threats, which are more targeted, harder to defend against, and more successful. The ITRC 2021 Data Breach Report captures this alarming reality in a review of the cyber compromises reported over recent years.
The third reason why cyberattack is such a big threat to businesses is its potential for devastation. A successful cyberattack can take a heavy financial toll on an organization, exact legal penalties, and ruin the brand’s reputation. IBM puts the average cost of a breach at $4.24 million. Cybercrime adds a $1 trillion drag on the global economy on a broader scale.
The first step to fighting cybercrime and preventing cyber incidents is understanding the threats out there. Threat intelligence helps organizations realize the security issues and risks they face and can, therefore, determine the relevant cybersecurity measures. In the spirit of threat awareness, we’ve compiled a list of the top cybersecurity threats to businesses and the best ways to safeguard organizations against them. Any of these candidates can be the biggest threat to cybersecurity.
Insider Threats
Top of the list is a big one: insider threats, which many organizations don’t take seriously enough. Insider threats lurk within the organization itself. They are caused by the actions of employees, contractors, business partners, or associates. Usually, these are careless mistakes, intentional sabotage, or negligence.
Forty-three percent of the employees surveyed in the Psychology of Human Error study said they had made mistakes that jeopardized cybersecurity in their organizations. Another survey done in the UK found that 88 percent of data breaches were actually caused by human error and not external cyberattacks.
The only way to eliminate insider threats is to foster a security-cautious culture throughout the organization. Begin by educating employees on the threat landscape and training everyone on cybersecurity best practices. Then minimize the internal security risk surface by reducing the number of privileged user accounts, instilling a level of security accountability in each individual, and awarding security clearance based on the employee’s job description.
Malware Attacks
Malware are notorious security threats to businesses. These are stealthy malicious software applications specially designed to steal information, sabotage IT processes, leech off computing resources, or clear pathways for secondary attacks. There are many different types of malware, including viruses, trojans, worms, bots, crypto miners, rootkits, and spyware.
Most malware are delivered through phishing emails, drive-by downloads, or compromised software applications. And they’re usually installed on endpoint devices (workstations, laptops, smartphones, etc.) by unsuspecting users. Controlling endpoints through remote monitoring and management can drastically reduce the risk of malware infections. Keeping a close eye on endpoints ensures that they are up to the expected security standards at all times. For instance, you want to be sure that OS, software, and antimalware tools are always up-to-date, and only authorized applications run on the devices. It’s also important to monitor network infrastructures for signs of potentially malicious traffic or requests.
Read Also:
Phishing
Phishing is one of the most widespread forms of cyberattacks on small businesses. Findings in the 2021 State of the Phish Report shows that about 74 percent of US organizations experienced a successful phishing attack in 2020. The report also depicts phishing as a gateway cyberattack, paving the way for threat actors to steal data, compromise user accounts, inject malware, or defraud individuals and organizations.
A phishing attack occurs when an attacker (phisher) pretends to be a trusted contact and tricks the victim into putting the organization at risk. Phishers typically convince their contacts (usually via email) to install malicious software, share sensitive information, or lower technical security defenses.
Employee security training is the most effective way to combat phishing and other social engineering attacks. Powerful spam email filters and web screeners also help to keep fraudsters away.
Ransomware
Ransomware is a type of malware that encrypts or steals a victim’s data and holds it hostage until a ransom is paid. This is one of the most devastating information security threats today. It takes, on average, $4.6 million to recover from a single ransomware attack (excluding the ransom itself, which can be as much as $50 million). However, paying the ransom does not always guarantee that the attacker will decrypt or restore the seized data.
To prevent ransomware attacks, you need a firm grip on endpoint security. This stops the underlying malware infection from taking hold in the first place. Since such attacks target data repositories, it’s always a good idea to protect all static data under a layer of impenetrable encryption. Also, data backups provide a vital workaround to ransomware attacks; you can simply restore backup copies if attackers manage to get hold of the original data.
Network Perimeter Breach
Nowadays, many corporate networks have multiple externally-facing nodes, which can cause serious security problems. With many employees now working from home, businesses have to open external network connections to keep remote employees and devices tethered to the main network. You may also find IoT devices with questionable security protocols connected directly to high-level corporate networks. Such connections can easily create security gaps on a network through which dangerous threats can slip undetected.
Here are some practical measures you can take to improve network security:
- Use VPNs to mask peripheral network connections.
- Deploy secure, standard remote assistance software to facilitate telecommuting.
- Isolate non-essential or unsecured devices from a protected network.
- Continuously monitor network traffic, behavior, and performance for early signs of an imminent cyber attack.
- Implement strong user authentication such as 2FA.
- Restrict lateral movement within the network.
Supply Chain Attacks
Supply chain attacks are among the top cybersecurity threats for small businesses. A supply chain attack compromises a company by targeting less secure third-party elements in the supply chain. Through these attacks, a threat actor can even infiltrate multiple organizations at once through third-party software applications and IT services.
These top internet security threats are nearly impossible to anticipate or prevent. You can never really tell where a supply chain attack could come from. For instance, hackers might exploit some unknown flaw in something as mundane as a PDF reader to steal sensitive documents.
The only way to minimize the risk of supply chain threats is to be wary of your business partners and the third-party entities in your supply chain. Scrutinize the security levels and guarantees of each IT-related service or product you bring into the company. It also helps to track software/service updates, and deploy patches and fixes to avoid falling victim to zero-day or other CVE-related exploits.
Final Thoughts
There is no denying the fact that all businesses, big and small, face some major information security threats. A recent survey found that cyberattacks on small businesses account for nearly half of the total attack volume. This tells you that no organization is immune to cybercrime. And since cyber threats are not going away any time soon, businesses will just have to learn to deal with these risks.
Luckily, there are several ways you can shrink your digital attack surface and reduce the risk of falling prey to threat actors. One of them is managing endpoint security. Securing and controlling remote endpoints is an easy and effective way to counter different forms of phishing, malware, and breach advances.
Action1 provides a robust, all-rounded endpoint management system with software deployment tools, real-time 24/7 monitoring, patch management services, and more features. The cloud-based architecture makes it ideal for handling remote endpoints in a hybrid work environment. And there’s more good news. On top of the affordable licenses, you can try Action1 for free with up to 100 endpoints. Sign up today and sample convenience, efficiency, freedom, and security in endpoint management.




